I have seen some places here and there that mention hacking cyberwere. I can see hacking some ones implanted comlink if it was on, but what could you really do with it.
-- you could access feeds from senseware.
-- mess with what some one see and hears through sound and vision links.
-- normal comlink hacking.
-- hack things the user has connected to his comlink
This all makes sense, but it seems like this could be streched to far. Shouldn't most cyberware be using a DNI, direct neural interface, and shouldn't a DNI be uneffcted by hacking. You shouldn't be able to choke someone to death with there own arm just because you hacked there comlink.
so I guess the questions are:
-- What is an implanted com really connected to.
-- Couldn't the comlink be setup to only accept commands from the DNI of the user. aka trusted computer system.
-- How hard is it to hack a skinlink network.
I am not sure how hacking some ones body would work, but I do know that any comlink I get will have and external power switch so I can turn the thing off if things go bad.
Full Version: Hacking Cyberware
| QUOTE (Egon) |
| -- What is an implanted com really connected to. -- Couldn't the comlink be setup to only accept commands from the DNI of the user. aka trusted computer system. -- How hard is it to hack a skinlink network. |
1. Typically, it would be the hub of their PAN
2. If you did that it would be useless for communication, and interacting with things outside the commlink.
3. If the network is purely skinlinked (ie. you can't hack their commlink and get into the skinlinked network that way) then it would require basically a very long handshake, or hiding a skinlinked device on them that also had signal.
| QUOTE (Egon) |
| -- Couldn't the comlink be setup to only accept commands from the DNI of the user. aka trusted computer system. -- How hard is it to hack a skinlink network. |
1) Yes. This is what hacking is - making the device believe it's receiving data from a legit source.
2) Well, typically a runner will have all his devices skinlinked, with only his commlink emitting wireless signals. That means the single possible point of entry is the commlink. If, for some reason, the person has a total skinlink with NO device emitting wireless signals, then you need physical contact - such as a long handshake or platin a bug on the person, as was mentionned,
| QUOTE (Backgammon) |
| 1) Yes. This is what hacking is - making the device believe it's receiving data from a legit source. 2) Well, typically a runner will have all his devices skinlinked, with only his commlink emitting wireless signals. That means the single possible point of entry is the commlink. If, for some reason, the person has a total skinlink with NO device emitting wireless signals, then you need physical contact - such as a long handshake or platin a bug on the person, as was mentionned, |
1. I would think it would be a little hard to spoof a DNI
2. Here are 3 quick ways to beat a skin link.
-- grabing then same rail on a metal staircase
-- a taser
-- plant a cheep comlink on them. or in their gun or in their car or anything else they might want to use.
| QUOTE (Egon) |
| 1. I would think it would be a little hard to spoof a DNI 2. Here are 3 quick ways to beat a skin link. -- grabing then same rail on a metal staircase -- a taser -- plant a cheep comlink on them. or in their gun or in their car or anything else they might want to use. |
1 is incorrect. I mean, sure, it's hard, but that's what the software is for. The hacking tests and the ratings used specifically represent you hacking whatever.
2. I'd have to re-read the skinlink description, but I highly doubt grabbin the same metal rail will do the trick. I don't think the signal travels by metal, just skin.
| QUOTE (Backgammon) |
| 2) Well, typically a runner will have all his devices skinlinked, with only his commlink emitting wireless signals. That means the single possible point of entry is the commlink. If, for some reason, the person has a total skinlink with NO device emitting wireless signals, then you need physical contact - such as a long handshake or platin a bug on the person, as was mentionned, |
I feel that this is the downfall fo hacking. Alot of the changes to SR4 I was worried about but I have seen then in action and accepted most of them as really good ways of cleaning up the system but I just see the hacking rules becoming this convaluted mess of having to micro manage what I have linked and what I have wireless and what IC I have running on what device and blah blah blah. I feel that this just puts the players into an overactive state of paranoia that ultimatly detracts from the rest of the game.
| QUOTE (Casper) |
| I feel that this is the downfall fo hacking. Alot of the changes to SR4 I was worried about but I have seen then in action and accepted most of them as really good ways of cleaning up the system but I just see the hacking rules becoming this convaluted mess of having to micro manage what I have linked and what I have wireless and what IC I have running on what device and blah blah blah. I feel that this just puts the players into an overactive state of paranoia that ultimatly detracts from the rest of the game. |
I agree, but that's pretty much how security goes. You try to think like hte hacker, and set up a defense that makes the hacker's job more difficult... but all the effort you put into it is pointless unless you think it is very likely that you will be hacked.
What I have seen is that a lot of my players have attempted to come up with a PAN that is neigh unhackable, but which they can still use for everything they want to - and so long as they don't wirelessly connect to anything, that is fine with me... but no matter what, if their equipment can communicate wirelessly with something (or with the matrix at all), I rule a hacker can do the same things, but backwards.
So, it essentially comes down to two set ups. Hackable with internet access? or Unhackable, and local only? The only real-world example I like is basically pulling the ethernet cable out of your computer (or turning off your wireless network adapter). You're safe from hacking, but your computer is totally gimped, and can only communicate with things that are plugged into it.
IMO, skinlinking is just another wire. The rules are even quiet on weather one skinlinked signal can jum pfrom one person's skin to another... my suspicion is that they will mention it in Unwired (sometime next year
| QUOTE (Egon) |
| This all makes sense, but it seems like this could be streched to far. Shouldn't most cyberware be using a DNI, direct neural interface, and shouldn't a DNI be uneffcted by hacking. You shouldn't be able to choke someone to death with there own arm just because you hacked there comlink. |
You are correct. Hacking a PAN or cyberware doesn't give you control over the DNI, but to control where the output goes (or doesnt).
| QUOTE |
1. -- What is an implanted com really connected to. 2. -- Couldn't the comlink be setup to only accept commands from the DNI of the user. aka trusted computer system. 3. -- How hard is it to hack a skinlink network. |
1. Implants are connected to a DNI that connects to you brain. You aren't hacking the DNI, but are hacking the device (the implant) the data comes into. Worst you could do is "Turn-off" cybereyes but I don't see any rules about being able to do as much.
2. Yes, but that's the whole point of hacking: Making a system/device think you are legit.
3. The hardest part of the Skinlink is the problem of Social Engineering yourself to be able to hack it. In terms of dice it's no harder, but you've got the whole problem of being able to use your dice.
| QUOTE |
| I am not sure how hacking some ones body would work, but I do know that any comlink I get will have and external power switch so I can turn the thing off if things go bad. |
And if someones goal is to hamper your ability to send/receive data (say videofeeds, bio-information, smartgun data) then it's mission accomplished.
Most cyberware doesn't really have a need to send/receive data but it is an option and like any good Firewall (of current times) you plug the holes that aren't being used and can be exploited.
I'm trying to wrap my mind about the sort of things hackers can do to unfortunate people. This is how I have things down in my mind. Do I have this about right?
A hacker is being shot at by some greasy punk. The greasy punk is connected to a comlink with Simsense, has a cyberarm, and Smartlink. The hacker spends a few turns behind cover hacking into the punk's comlink. The hacker can then:
Use the Edit command to remove the hacker from the punks vision.
Use the Command command to eject the clip from his smartlinked gun.
Attack his Smartlink program, trying to shut it down.
Use the Command command on his cyberarm to turn the gun on his own head.
Attack the OS for his Cyberarm, shutting it down untill it has a chance to reboot.
Use the Edit command to make the ganger's buddies running up to help look like Lone Star officers.
If he had Cyberlegs the hacker could use the Command command to make him run away.
If he had Cyber eyes or Ears the hacker could attack their Icon on the Commlink, shutting them down.
If he was running his Commlink simsense with full emotional range the hacker could make him feel frightened of him.
Are these all viable things the hacker could do to this guy? With the cyberware, does the hacker just have to hack into the Commlink or does he have to hit the Commlink and then hack into the arm to attack it there?
A hacker is being shot at by some greasy punk. The greasy punk is connected to a comlink with Simsense, has a cyberarm, and Smartlink. The hacker spends a few turns behind cover hacking into the punk's comlink. The hacker can then:
Use the Edit command to remove the hacker from the punks vision.
Use the Command command to eject the clip from his smartlinked gun.
Attack his Smartlink program, trying to shut it down.
Use the Command command on his cyberarm to turn the gun on his own head.
Attack the OS for his Cyberarm, shutting it down untill it has a chance to reboot.
Use the Edit command to make the ganger's buddies running up to help look like Lone Star officers.
If he had Cyberlegs the hacker could use the Command command to make him run away.
If he had Cyber eyes or Ears the hacker could attack their Icon on the Commlink, shutting them down.
If he was running his Commlink simsense with full emotional range the hacker could make him feel frightened of him.
Are these all viable things the hacker could do to this guy? With the cyberware, does the hacker just have to hack into the Commlink or does he have to hit the Commlink and then hack into the arm to attack it there?
I would say you could do the eject the clip, shutdown the Smartlink, Edit to look like Lone Star officers, shutdown the cybereyes/ears, and overload his sim module actions. The other actions that pertain to the cybereyes or cyberlimbs wouldn't work. There isn't any real reason to have your cyberarm or cyberlegs meshed into your network unless you are running diagnostics on them, which usually doesn't happen during combat.
I think that something that is hardwired through DNI, like cybereyes, can't be spoofed/shutdown. It's wireless feed, if it is broadcasting, can be edited or jammed but the cybereyes themselves can't be "turned off". The user wouldn't receive the input from their smartlink but they can still see the target and shoot it. No way would someone broadcast their eye's "command code" so that someone could shut them down. That's why I would say cyberlimbs can't be hacked and turned against their owners, unless the person has them broadcasting wirelessly (which makes no sense) or hooked to their PAN (which also makes no sense unless their are running diagnostics). And even if the cyberlimb gets hacked, the brain has priority input over the wireless input so the person who owns the cyberlimb can simply just turn off wireless function and sever the hacker's attack. This also includes other cyberware that wouldn't even be wireless, such as Wired Reflexes, a tooth compartment or muscle augmentation.
I would give the hackee the chance to use a free action and turn off wireless once they realize their arm is trying to choke them. Once they do, the arm returns to normal because the brain has priority over any other input. IMHO only.
I think that something that is hardwired through DNI, like cybereyes, can't be spoofed/shutdown. It's wireless feed, if it is broadcasting, can be edited or jammed but the cybereyes themselves can't be "turned off". The user wouldn't receive the input from their smartlink but they can still see the target and shoot it. No way would someone broadcast their eye's "command code" so that someone could shut them down. That's why I would say cyberlimbs can't be hacked and turned against their owners, unless the person has them broadcasting wirelessly (which makes no sense) or hooked to their PAN (which also makes no sense unless their are running diagnostics). And even if the cyberlimb gets hacked, the brain has priority input over the wireless input so the person who owns the cyberlimb can simply just turn off wireless function and sever the hacker's attack. This also includes other cyberware that wouldn't even be wireless, such as Wired Reflexes, a tooth compartment or muscle augmentation.
I would give the hackee the chance to use a free action and turn off wireless once they realize their arm is trying to choke them. Once they do, the arm returns to normal because the brain has priority over any other input. IMHO only.
I'm wondering if you'd be able to hack something like a Cyberarm at all, to be completely honest. In modern day networking, if a system doesn't need to be put on a network, it isn't. Plain and simple. Not strictly from a logical/subnet/VLAN isolation, but actually keeping the system physically disconnected from other systems outside of it's network.
What motivation would someone with Cyberware benefit from having the electronic signals from their cyberarm transmit to their comlink? Realistically, probably none. And while -equipment- inside of a cyberarm may be wired into a comlink, that's hardly the same thing as having full run of someone's 'cyberarm', including functions like movement, strength, etc.
-Perhaps- it'd be possible to decipher signals between the cybernetic arm, and brain, if the signals from one line were induced into the wirelessly available line, but what should really be seperating one system, from another, in networked environment like a human being, is the brain itself - Until you can hack someone's brain, you're asking for some serious suspension of disbelief.
The relative security of 'going under the knife' for firmware upgrades or patches, far outweight any benefit of wirelessly downloading them into the isolated systems of cyberware.
Now - Systems that require wireless interaction are a different matter. Having Smartlink wireless Goggles, rather than a hardlined Smartlink, could be hacked, for instance.
But all the rest. Enh. Doubtful. Really doubtful.
What motivation would someone with Cyberware benefit from having the electronic signals from their cyberarm transmit to their comlink? Realistically, probably none. And while -equipment- inside of a cyberarm may be wired into a comlink, that's hardly the same thing as having full run of someone's 'cyberarm', including functions like movement, strength, etc.
-Perhaps- it'd be possible to decipher signals between the cybernetic arm, and brain, if the signals from one line were induced into the wirelessly available line, but what should really be seperating one system, from another, in networked environment like a human being, is the brain itself - Until you can hack someone's brain, you're asking for some serious suspension of disbelief.
The relative security of 'going under the knife' for firmware upgrades or patches, far outweight any benefit of wirelessly downloading them into the isolated systems of cyberware.
Now - Systems that require wireless interaction are a different matter. Having Smartlink wireless Goggles, rather than a hardlined Smartlink, could be hacked, for instance.
But all the rest. Enh. Doubtful. Really doubtful.
For implanted cyberware:
I can easily see eject the clip from a smart weapon, and maybe a loop making any clip inserted immediately drop out of the weapon.
I can also see moving the aiming point off on the smartlink, giving a negative penalty until the user turn off the smartlink.
If you have an implanted Commlink, that can be hacked, as has wireless capability, and hooked up to your DNI system.
Communications with the rest of your team can be hacked.
I can easily see eject the clip from a smart weapon, and maybe a loop making any clip inserted immediately drop out of the weapon.
I can also see moving the aiming point off on the smartlink, giving a negative penalty until the user turn off the smartlink.
If you have an implanted Commlink, that can be hacked, as has wireless capability, and hooked up to your DNI system.
Communications with the rest of your team can be hacked.
The problem is that the Direct Neural Interface is precisely that - A direct Neural Interface. I'm not sure how familiar any of you may be with Network Topologies, but the Brain would act similiar to a Router (Layer 3), while the DNI would have traffic passing through the Virtual LANs of a switch (Layer 2).
Layer 2 devices can't talk directly to each other if they are on seperate Virtual Local Area Networks, and must go through a gateway, the Layer 3 device, which is the human brain, in this case.
This Effectively means that different pieces of the same hardware can co-exist in the same 'box', without actually having direct connectivity between them, as they would be logically seperated from each other. If this is a standard security measure -today-, then I can only imagine how much tighter network security can become.
You're operating under the assumption that because the Comlink is physically (Layer 1) connected to a port of the DNI, which is in turn physically connected through a different port, than if you can spoof data packets to one, you can likewise spoof them to another. Unfortunately, that's a false assumption. And this is where things like port specific access-lists come into play, which essentially do the follow: "Your type of traffic belongs here. ALLOWED." - "Your type of traffic does not belong here. DENIED." End of story. And even if you spoofed data packets into a port, past it's access list, you're using input types that are allowed on that port, like wireless input for targetting systems, whereas data packets for something like 'Ejecting a Clip' wouldn't be valid traffic, unless you were able to change the DNI port access lists.
And the reason you can't change the DNI port access lists, is because the DNI management information is kept on yet another logically seperated network, directly interfacing with the brain. Short of physically putting someone under the knife, and altering their firmware, or effectively hacking through their brain, you're up shit's creek.
--------------------
The Following is a heavily simplified example of what a Commlink, Smartlink, Cyberarm, and Wired Reflexes network, interfacing through a DNI would look like.
Physical Connections: Comlink --> DNI, Smartlink --> DNI, Cyberarm --> DNI, Wired Reflexes --> DNI, Human Brain --> DNI.
*Note that each cybernetic modification acts like an end user, while the DNI acts as a data packet switching device; The central hub, for each spoke of the network. The human brain is the device that allows connectivity -between- devices.
Logical Connections over Physical Connections
Commlink (Wireless Communication) Virtual Network --> DNI Logical Port 1
Commlink (Augmented Reality Filter) Virtual Network --> DNI Logical Port 2
Smartlink (Augmented Reality Filter) Virtual Network --> DNI Logical Port 3
Smartlink (Fine Motor Skill Adjustment) Virtual Network --> DNI Logical Port 4
Cybernetic Arm (Motor Controls) Virtual Network ---> DNI Logical Port 5
Human Input/Processing/Output --> DNI Logical Port 6
DNI Management Virtual Network ---> DNI Logical Port 7
**With the exception of the cyber-arm, each physical connection carries multiple logical isolated networks, and while there may be a single physical port, the data is still disected and seperated by the DNI interface.
Access-List All - Allow All communication to/from DNI Logical Port 6, Human Brain
Access-List Logical Port 1 - Firewall Software here, as this is link to ourside world.
Access-List Logical Port 2 - Allow Communication to/from Port 1&3, Deny all else.
Access-List Logical Port 3 - Allow Communication to/from Port 1&2, Deny all else.
Access-List Logical Port 4 - Allow Communication to/from Port 5, Deny all else
Access-List Logical Port 5 - Allow Communication to/from Port 4, Deny all else
Access-List Logical Port 6 - Allow communication to all ports, ignore implicit Deny
Access-List Logical Port 7 - Allow communication to/from Port 6
***Heavy simplified accesslist. In reality, they're long lists of IP addresses, and available ports, both physical, and logical - Notice that The Human Brain network can interface with all other networks, and so, all communication can pass -through- the human brain. Also note that while Augmentation Reality networks can discuss data together independant of the human brain, and Smartlink Fine Motor Skills and Cybernetic motion controls can talk to each other, those different network types are isolated.
At the end of the day, I suppose it'd be possible for 'backdoors' to be left open for sloppy second hand pieces of cyberware. And periodically, a DNI firmware package would need to be upgrade to include new patches for known compatibility issues, or port security problems. But really, the -vast, vast, vast, vast- majority of the time, it just simply isn't possible to 'hack' through an entire device, because each function should be assigned to it's own network of information.
Layer 2 devices can't talk directly to each other if they are on seperate Virtual Local Area Networks, and must go through a gateway, the Layer 3 device, which is the human brain, in this case.
This Effectively means that different pieces of the same hardware can co-exist in the same 'box', without actually having direct connectivity between them, as they would be logically seperated from each other. If this is a standard security measure -today-, then I can only imagine how much tighter network security can become.
You're operating under the assumption that because the Comlink is physically (Layer 1) connected to a port of the DNI, which is in turn physically connected through a different port, than if you can spoof data packets to one, you can likewise spoof them to another. Unfortunately, that's a false assumption. And this is where things like port specific access-lists come into play, which essentially do the follow: "Your type of traffic belongs here. ALLOWED." - "Your type of traffic does not belong here. DENIED." End of story. And even if you spoofed data packets into a port, past it's access list, you're using input types that are allowed on that port, like wireless input for targetting systems, whereas data packets for something like 'Ejecting a Clip' wouldn't be valid traffic, unless you were able to change the DNI port access lists.
And the reason you can't change the DNI port access lists, is because the DNI management information is kept on yet another logically seperated network, directly interfacing with the brain. Short of physically putting someone under the knife, and altering their firmware, or effectively hacking through their brain, you're up shit's creek.
--------------------
The Following is a heavily simplified example of what a Commlink, Smartlink, Cyberarm, and Wired Reflexes network, interfacing through a DNI would look like.
Physical Connections: Comlink --> DNI, Smartlink --> DNI, Cyberarm --> DNI, Wired Reflexes --> DNI, Human Brain --> DNI.
*Note that each cybernetic modification acts like an end user, while the DNI acts as a data packet switching device; The central hub, for each spoke of the network. The human brain is the device that allows connectivity -between- devices.
Logical Connections over Physical Connections
Commlink (Wireless Communication) Virtual Network --> DNI Logical Port 1
Commlink (Augmented Reality Filter) Virtual Network --> DNI Logical Port 2
Smartlink (Augmented Reality Filter) Virtual Network --> DNI Logical Port 3
Smartlink (Fine Motor Skill Adjustment) Virtual Network --> DNI Logical Port 4
Cybernetic Arm (Motor Controls) Virtual Network ---> DNI Logical Port 5
Human Input/Processing/Output --> DNI Logical Port 6
DNI Management Virtual Network ---> DNI Logical Port 7
**With the exception of the cyber-arm, each physical connection carries multiple logical isolated networks, and while there may be a single physical port, the data is still disected and seperated by the DNI interface.
Access-List All - Allow All communication to/from DNI Logical Port 6, Human Brain
Access-List Logical Port 1 - Firewall Software here, as this is link to ourside world.
Access-List Logical Port 2 - Allow Communication to/from Port 1&3, Deny all else.
Access-List Logical Port 3 - Allow Communication to/from Port 1&2, Deny all else.
Access-List Logical Port 4 - Allow Communication to/from Port 5, Deny all else
Access-List Logical Port 5 - Allow Communication to/from Port 4, Deny all else
Access-List Logical Port 6 - Allow communication to all ports, ignore implicit Deny
Access-List Logical Port 7 - Allow communication to/from Port 6
***Heavy simplified accesslist. In reality, they're long lists of IP addresses, and available ports, both physical, and logical - Notice that The Human Brain network can interface with all other networks, and so, all communication can pass -through- the human brain. Also note that while Augmentation Reality networks can discuss data together independant of the human brain, and Smartlink Fine Motor Skills and Cybernetic motion controls can talk to each other, those different network types are isolated.
At the end of the day, I suppose it'd be possible for 'backdoors' to be left open for sloppy second hand pieces of cyberware. And periodically, a DNI firmware package would need to be upgrade to include new patches for known compatibility issues, or port security problems. But really, the -vast, vast, vast, vast- majority of the time, it just simply isn't possible to 'hack' through an entire device, because each function should be assigned to it's own network of information.
Well, the ejecting clip and off setting the aiming point were directed at the weapon, not the implanted commlink or such.
As for the human brain being the router, I understand (or think I do, being barely computer literate ), but, the human brain is not doing/making/understanding every line of code, it is basilcally hitting pre-programmed buttons that get the device to do what it want's too.
), but, the human brain is not doing/making/understanding every line of code, it is basilcally hitting pre-programmed buttons that get the device to do what it want's too.
Ex.: sending an video clip that you recorded from your cybereyes over your commlink to a buddy across room/town/continent/etc..
You do not think edit file XXX from frame 2341 to frame 6781, compress data, link to commlink, "dial" YYY address, send, confirm receipt, etc...
You think "Oh, I want to send this to Smokey, this will make his day", so, from "here" to "here", send to Smokey.
Your implanted hardware/software does all the work. If your Commlink is connected to you, any signal comming in has to be veried against "authorized" file, which is a computer file, hence "spoofable".
Oh, you can limit access by using various passcodes, say to shut down your cyberarm, causing the hacker to spend a few extra IPs to bypass each one.
That is why they say to have a good firewall on your implanted (or external) Commlink, to prevent this sort of thing.
As for the human brain being the router, I understand (or think I do, being barely computer literate
Ex.: sending an video clip that you recorded from your cybereyes over your commlink to a buddy across room/town/continent/etc..
You do not think edit file XXX from frame 2341 to frame 6781, compress data, link to commlink, "dial" YYY address, send, confirm receipt, etc...
You think "Oh, I want to send this to Smokey, this will make his day", so, from "here" to "here", send to Smokey.
Your implanted hardware/software does all the work. If your Commlink is connected to you, any signal comming in has to be veried against "authorized" file, which is a computer file, hence "spoofable".
Oh, you can limit access by using various passcodes, say to shut down your cyberarm, causing the hacker to spend a few extra IPs to bypass each one.
That is why they say to have a good firewall on your implanted (or external) Commlink, to prevent this sort of thing.
| QUOTE (Mistwalker @ Sep 22 2006, 07:03 AM) |
| As for the human brain being the router, I understand (or think I do, being barely computer literate |
You're partially correct. Perhaps I was a bit hasty to label the Human Brain as the Layer 3 device. The Human Brain is sending Input, and interpreting Output from the DNI - Not necessarily bridging the gap.
After some additional consideration on the subject, the DNI will operate as both a Layer2/Layer3 device, but those functional levels will still be isolated from each other. Augmented Reality will still exist on an isolated network from Fine Motor control. And the two won't have any need to interact with each other, and so will still be kept seperate from each other thanks to access-lists on logical ports.
DNI management, however, will still be a strictly 'hands-on' arrangement, requiring either a dedicated datajack, or actual surgery, and reflashing of the configuration firmware.
So, adjusting the previous model to take that into account, each 'function' from any given device connected to the DNI is -still- going to be isolated. And unless that function is reliant on wireless outside access for some reason will be unhackable unless someone intentionally messed with your firmware DNI configs on your last trip under the knife, and FUBAR'd your access-lists.
Really. Think about it. You're a samurai - What benefit would you have from networking the way your foot moves with the same network that surfs the wireless matrix for you? Can you think of one? Probably not. Access/Security are often a trade off, especially when it comes to networking - But when there is no purpose for access, it's a clear cut victory for security.
Well, all installed cyberware is wired internally for communication, too.
| QUOTE |
| Well, all installed cyberware is wired internally for communication, too. |
Yeah, but being 'wired together' is entirely different than being 'connected' in the sense that it's being discussed, above. Are electrical signals being passed between equipment? Yes - They're wired together. As those electrical signals still logicially isolated based on a function oriented logical network scheme? Absolutely. And can the distant device reject packets from sources that aren't allowed to pass data according to their access-lists? You betcha.
Let me see if I can whip up a metaphor, so people aren't lost in any technical jargon being presented.
Well, everything will be networked together in your body, as you need to be able to give it orders, be they concious orders or unconcious or motor reflex orders or combinations of the above.
I can see circumstances where you would want to lock your cyberleg in place, so you need to be able to tell it to do so, as well of it working by unconcious actions of walking, running, squatting, etc..
Components need to be able to talk to the router. If you can hack in thru a component, you can talk to the router, and possibly spoof it. But, as I said, would take more than one hack to get to your cyberarm. While he was doing that, the sammy would be doing his best to kill him, or punt him from his system.
I can see circumstances where you would want to lock your cyberleg in place, so you need to be able to tell it to do so, as well of it working by unconcious actions of walking, running, squatting, etc..
Components need to be able to talk to the router. If you can hack in thru a component, you can talk to the router, and possibly spoof it. But, as I said, would take more than one hack to get to your cyberarm. While he was doing that, the sammy would be doing his best to kill him, or punt him from his system.
| QUOTE (Steak and Spirits) |
| Yeah, but being 'wired together' is entirely different than being 'connected' in the sense that it's being discussed, above. Are electrical signals being passed between equipment? Yes - They're wired together. As those electrical signals still logicially isolated based on a function oriented logical network scheme? Absolutely. And can the distant device reject packets from sources that aren't allowed to pass data according to their access-lists? |
Not really. If you want to be secure without actually disconnecting wires, shut down the interface. Everything else can be exploited.
This isn't really a problem, though, as you always have hands-on access to your ware through DNI.
| QUOTE |
| Components need to be able to talk to the router. If you can hack in thru a component, you can talk to the router, and possibly spoof it. But, as I said, would take more than one hack to get to your cyberarm. While he was doing that, the sammy would be doing his best to kill him, or punt him from his system. |
Talking -through- a router, and talking -to- a router are two very, very, very different things. So no. Definitively no. If this were possible, then Shadowrun 4th edition would be set in an alternate universe where network security did not exist.
For all intents and purposes, if you can't stick your physical hand on a router, you shouldn't be able to interact with it's function one iota.
| QUOTE |
| Not really. If you want to be secure without actually disconnecting wires, shut down the interface. Everything else can be exploited. |
The point is that the interface doesn't need to be shutdown. Only logical ports on the interface need to be shutdown.
Shutting down the interface would sever communication completely. Since that isn't a -good- thing, logical ports (As opposed to physical ports) are shutdown.
You can read up on TCP/IP and UDP ports Here.
| QUOTE (Steak and Spirits) |
| Talking -through- a router, and talking -to- a router are two very, very, very different things. So no. Definitively no. If this were possible, then Shadowrun 4th edition would be set in an alternate universe where network security did not exist. |
Routers suffer the same problems any software distributing information suffers... you can attack routers through buffer overflows and the like.
| QUOTE (Steak and Spirits) |
| For all intents and purposes, if you can't stick your physical hand on a router, you shouldn't be able to interact with it's function one iota. |
Tell that to Cisco.
| QUOTE (Steak and Spirits) |
| The point is that the interface doesn't need to be shutdown. Only logical ports on the interface need to be shutdown. Shutting down the interface would sever communication completely. Since that isn't a -good- thing, logical ports (As opposed to physical ports) are shutdown. |
Sure... but that still leaves you open to attacks of the lower levels of network communication.
| QUOTE |
| Routers suffer the same problems any software distributing information suffers... you can attack routers through buffer overflows and the like. |
That's entirely different. And in either case, you're still not talking -to- the router. You're just filling up the network with garbage so communication can't get through. You can't flood a network to change a routing protocol configuration anymore than you can flood a network to make a printer start printing pages.
You aren't doing anything functional in that case. You're just taking advantage of poor filtering.
| QUOTE |
| Tell that to Cisco. |
Why? They're perfectly aware that without setting up remote management capabilities their switching systems are unmanageable excepting physical connection through the console port. Afterall, that's why they include a console port to begin with. So that a device that can't be interfaced with remotely due to network outages can be directly interfaced with through a serial connection.
| QUOTE |
| Sure... but that still leaves you open to attacks of the lower levels of network communication. |
The only attacks that could feasibly be launched against a logically isolated network would be attacks that involved destroying the ability for packets to travel the physical line. This is because for all intents and purposes, the only thing that touches the networks is that physical line, and all other ties, to include process, are severed.
| QUOTE (Steak and Spirits) |
| That's entirely different. And in either case, you're still not talking -to- the router. |
No, it's not - if you manage to trigger a buffer overflow on a system, you can use it to run code on it... and open up remote access.
| QUOTE (Steak and Spirits) |
| Why? |
Because they are patching up holes in their traffic analysis, firewalls, etc?
| QUOTE (Steak and Spirits) |
| The only attacks that could feasibly be launched against a logically isolated network would be attacks that involved destroying the ability for packets to travel the physical line. |
Sure, but as soon as you are part of the network, you can spoof packet to look like they are for the legitimate port from the legitimate devices... usually in a MitM attack style.
i would say theres some basic things you cannot do... you cannot make a man hold a gun to his own head. that cyberlimb is like a real arm, as far as the brain is concerned. the most you could do is play with things inside the arm- open compartments, extend/retract blades, fire guns, and cycle the gyro-stabilizer. if its just a basic arm (no extra goodies) then it dont do much.
with eyes... you can probably do pop-ups like crazy, but not much else. Think of your brain-eye conection being like you sitting at a computer. the hacker can make popups, and screw with some settings... but not much else. but popups with a sim component can be very distracting... especialy gay troll S&M porn. so you cant see and you getting some very disturbing sim all of a sudden... effective enough. maybe make your oponent waste an action closing it.. or more if it a virus that keep opening new popups.
cyberware is not just some machine... its a part of he body, and as such responds only to input from the brain for many functions. you cannot hack the brain, the best you can do is send inputs to a person... which can get diferent results. the best you can do is to hack those parts which do respond to outside control- things that say 'yes the commlink can tell me what to do'. things like the image link in the eyes, the commlinks sim module, and various other senseware inputs.
with eyes... you can probably do pop-ups like crazy, but not much else. Think of your brain-eye conection being like you sitting at a computer. the hacker can make popups, and screw with some settings... but not much else. but popups with a sim component can be very distracting... especialy gay troll S&M porn. so you cant see and you getting some very disturbing sim all of a sudden... effective enough. maybe make your oponent waste an action closing it.. or more if it a virus that keep opening new popups.
cyberware is not just some machine... its a part of he body, and as such responds only to input from the brain for many functions. you cannot hack the brain, the best you can do is send inputs to a person... which can get diferent results. the best you can do is to hack those parts which do respond to outside control- things that say 'yes the commlink can tell me what to do'. things like the image link in the eyes, the commlinks sim module, and various other senseware inputs.
| QUOTE (Rotbart van Dainig) | ||
No, it's not - if you manage to trigger a buffer overflow on a system, you can use it to run code on it... and open up remote access. |
I'm with Rotbart here.
Traditionally, no you can't interface with the router. But that's the point of a number of different attacks. They use overflows to activate code as though you were interfacing with the router.
Granted, you can make some reasonable assumptions about the improvements in security over the years, but you can also make the same reasonable assumptions about the improvements in hacking.
I think it's just fine to talk about things in modern terms, because improvements in both tend to keep pace. Physical separation is the only real security.
I'm reminded of a logging machine I set up at an old job. We wanted 100% to know that the logs on that machine were accurate and untampered reports. We knew the data that it was sent might be compromised, but we wanted to know that the data was preserved in its original state.
So we stripped the ether cable down to only the send wires. At that point, the machines sending the logs were just shipping them blindly - if the logging machine had a failure, it couldn't tell the logger. But at the same time, the logger couldn't interact with the machine in any way but to send.
If someone had known our setup, they could have hacked it - simply transmit a program that doesn't require input, and just runs. But no one knew about it, so it worked when we got hacked.
| QUOTE (lorechaser) |
| If someone had known our setup, they could have hacked it - simply transmit a program that doesn't require input, and just runs. But no one knew about it, so it worked when we got hacked. |
Ah, the old ST about a one-way SAN being hacked by sending in a smartframe...
| QUOTE (Rotbart van Dainig) | ||||
No, it's not - if you manage to trigger a buffer overflow on a system, you can use it to run code on it... and open up remote access.
Because they are patching up holes in their traffic analysis, firewalls, etc?
Sure, but as soon as you are part of the network, you can spoof packet to look like they are for the legitimate port from the legitimate devices... usually in a MitM attack style. |
Not really. This model would effectively be hardware based switching. You're not going to be able to h@x0r it's configuration - Like I said, I agree that you could pump gargage into the Personal Area Network, but not edit configurations.
These configurations aren't -on the network-. They aren't stored in memory that pertains to any function -on the network-. So talking about setting up configurational changes -through the network- is silly. Totally ridiculous, infact.
Buffer overflows are kind of like subliminal messages snuck into commercials on TV. It might be a great way to sneak little thoughts or notions into the people that see them. But if your TV is tuned into another channel, your aren't going to see that commercial. Sorry. That's all she wrote.
So, what it boils down to is - Yes, like I said, you can hack things inside of the same network. No - You can't hit the rest.
And God forbid that instead of logical seperation of trunking data on one transmission medium, they just ran individual wires to their own ports. Because then, there would be even less room for 'hacking' to occur as you're describing it.
| QUOTE (Steak and Spirits) |
| These configurations aren't -on the network-. They aren't stored in memory that pertains to any function -on the network-. So talking about setting up configurational changes -through the network- is silly. Totally ridiculous, infact. |
Look, those configurations are stored on the router and the router runs it minimalistic OS that does jobs like traffic analysis, etc.
So, once you managed to send packets that somehow produce a hickup in the traffic monitoring software, you can run code on the router. Then, you go from there, change configuration, open remote access, etc.
What you are talking about is a not too bright network switch that has no configuration to speak of.
| QUOTE (Rotbart van Dainig) | ||
Look, those configurations are stored on the router and the router runs it minimalistic OS that does jobs like traffic analysis, etc. So, once you managed to send packets that somehow produce a hickup in the traffic monitoring software, you can run code on the router. Then, you go from there, change configuration, open remote access, etc. What you are talking about is a not too bright network switch that has no configuration to speak of. |
No, I think he's talking about a router with configurations hardcoded into some sort of read-only memory module which is queried whenever a configuration question comes up. So it takes physical access to change the configuration, because you need to pull the module and replace it with a new one or use some sort of special hardware to rewrite it. There may be some sort of vulnerability to redirecting the config queries to a new location, but rewriting that much code through a buffer overrun is questionable.
edit to add: There's also the question of packet denial based on physical interface. That is, if I have a bog-standard replacement cyberarm with no special components, I can set it up to simply drop all packets coming in through the wireless interface. Or just turn off/remove the stupid wireless interface, since it should be wired into my CNS directly. Same for any direct functionality built into the cyberarm. Why route the trigger for that gyromount through the commlink (either wireless or skinlink)? Or the command functions for a cyber weapon?
..only if those aren't loaded into RAM.
| QUOTE (Rotbart van Dainig) |
| ..only if those aren't loaded into RAM. |
You mean the configs? That's what I meant by having the module queried whenever the configuration is required. So instead of having, frex, the firewall rules loaded into RAM, they're accessed directly from the configuration module whenever a packet comes in (and we can assume the access links are optimized and so forth). You could introduce some sort of memory resident program that intercepts the queries and delivers changed responses, I guess, but that seems a bit much for a buffer overrun.
That really depends on the exploit - you indeed could install a backdoor, and go from there.
| QUOTE (Rotbart van Dainig @ Sep 22 2006, 04:15 PM) |
| That really depends on the exploit - you indeed could install a backdoor, and go from there. |
I guess. Wouldn't the backdoor still be limited by the logical access rules until you got something into RAM that either pre-processed incoming packets or post-processed the returned firewall rules, though?
Of course, you could simply regard all this crap as the Hacking+Exploit Vs firewall test
That's exactly where this thread was heading to - there are rules for a reason. 
| QUOTE |
| That really depends on the exploit - you indeed could install a backdoor, and go from there. |
Your installation of a backdoor will be limited to functions that you can interface with. Which is why I'm not disputing that the functions of a Smartlink that interfaces with a comlink can be disrupted.
At best, however, all you'd manage the router to do in regards to other functions is reboot.
So, you can load up your cyberlimb with IC and anti-hack Agents? Can you install a Firewall on a cyberlimb? Firewall 6 is only 3000 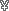 so I don't see many people having a problem with it. IC and Agents might send you back some though.
so I don't see many people having a problem with it. IC and Agents might send you back some though.
Yes, that's the whole idea of cyberware having a device rating...
| QUOTE (WhiskeyMac) |
| So, you can load up your cyberlimb with IC and anti-hack Agents? Can you install a Firewall on a cyberlimb? Firewall 6 is only 3000 |
Well, I maintain that there is no reason for a cyberlimb in and of itself to have a wireless link. Single modules in the limb may require one, but all cyberlimb functions should be controlled by DNI through the existing nerves at the mount point. The only thing that might require a wireless link is some sort of data intensive sensor system installed in the limb.
| QUOTE (Rotbart van Dainig) |
| That's exactly where this thread was heading to - there are rules for a reason. |
Nah. The whole thread was heading towards demostrating that some functions would have interconnectivity, while others would not. And that interconnectivity between devices, is not the same as interconnectivity between functions.
And that each function would interface independently of the device itself.
Re: One 'box' with information travelling down seperate, isolated paths.
| QUOTE (p. 213 sr4) |
Device Rating (Universal) There are far too many electronics in the world of Shadowrun for a gamemaster to keep track of their individual Matrix attributes. Instead, each device is simply given a Device rating. Unless it has been customized or changed in some way, assume that each of the Matrix attributes listed above for a particular device equals its Device rating. If a particular device plays an important role in an adventure, the gamemaster should assign a full complement of Matrix attributes to it. If the item only plays a passing role, then a simple Device rating will suffice. The Sample Devices table (p. 214) lists typical Device ratings for common electronics. |
The "attributes above" are response, signal, firewall, and system - the table describes standard cyberware as a rating 3 device, alphaware as rating 4, betaware as 5, and deltaware as 6.
In other words - your cyberlimb already has a firewall of 3 installed, which is its max, unless the GM allows you to upgrade your cyberware's system and response attributes.
A cyberlimb doesn't need a firewall. It isn't connected to anything outside of it's own iternal network path to the brain.
A firewall would be used for a device that accepts ouside input.
A firewall would be used for a device that accepts ouside input.
| QUOTE (Steak and Spirits) |
| The whole thread was heading towards demostrating that some functions would have interconnectivity, while others would not. And that interconnectivity between devices, is not the same as interconnectivity between functions. |
A demonstration, that, given the rules of SR4, would utterly fail.
| QUOTE (Rotbart van Dainig) | ||
A demonstration, that, given the rules of SR4, would utterly fail. |
Elaborate.
I have to admit that I have lost track of this discussion some while back. I think it was when someone said that the human brain is a router. I just wanted to point out that on Page 204 under "Other Hacker Tricks" the books specifically says a hacker can turn a street sam's own cyberarm against him. The black box on 224 also says that cyberlimbs are hackable.
I don't know why cyberlimbs and other items of personal equipment that are not commlinks would be on the network. My personal interpretation is that the rules were written by two people. One person wanted hacking to be like Ghost in the Shell, and wrote the rules in such a way that hackers can do things like take control of someone else's eyes. Another guy wrote the rules thinking that he did not want to be choked to death by his own cyberarm so he made it extremely easy and practical to take all of that crap off of the network. Really, you can only have it one way.
I don't know why cyberlimbs and other items of personal equipment that are not commlinks would be on the network. My personal interpretation is that the rules were written by two people. One person wanted hacking to be like Ghost in the Shell, and wrote the rules in such a way that hackers can do things like take control of someone else's eyes. Another guy wrote the rules thinking that he did not want to be choked to death by his own cyberarm so he made it extremely easy and practical to take all of that crap off of the network. Really, you can only have it one way.
| QUOTE |
| NETWORK SECURITY Though wireless networks are easier, they are also a security vulnerability. While it’s true that most megacorps prefer to avoid cable spaghetti, they do use “cold storage” wired systems in order to isolate them from outside wireless networks and intrusion. In order to access such networks, a hacker needs to gain access to a physical jackpoint or terminal. page 223, SR4 |
Seems like the precedent is always set in SR4, if it hadn't already been heavily anchored in reality to begin with - Except in this case, hard wires, and 'wifi absorbing paint' is replaced with logical isolation of functions between cybernetic networks.
In this case, the 'jackpoint' is physically on the device. You can get there by surgery.
In which case, the device has no wireless or wired connection at all... that's the precedent.
And the point is that connections in SR4 rules are established between devices, not functions.
And the point is that connections in SR4 rules are established between devices, not functions.
| QUOTE |
| And the point is that connections in SR4 rules are established between devices, not functions. |
Yes, physical connections. Are you having difficulty understanding the difference between a logical, and physical connection?
No, just connections.
In fact, the rules treat clusters the same way as single interfaces.
In fact, the rules treat clusters the same way as single interfaces.
So you are saying that in 2070, technology has advanced to the point where it emulates the 1970s?
Please provide an example.
Please provide an example.
Take the smartgun - it is one device, yet it features a rangefinder and a camera.
Those are single devices themselves, unless installed in a greater sensor-package, at which point they are one device combined.
Those are single devices themselves, unless installed in a greater sensor-package, at which point they are one device combined.
This is a "lo-fi" version of our main content. To view the full version with more information, formatting and images, please click here.