Full Version: Luddite Ninja Shadowrunners Vs. E-War Commando's
| QUOTE (silentmaster101) |
| i think i got it off amazon, IIRC. wasnt too long ago, maybe a month or so. edit: might be v3, im looking at the hardback book right now so im a bit fuzzy on it. |
look a little closer... the column that starts off as "response" changes to "device rating" and the column that starts off as "signal" changes to "availability" about halfway down the table.
it fooled me too, at first, until they pointed out the change
| QUOTE (hobgoblin) |
| i wonder what the difference between the stealth tag and a comlink on hidden is... |
Nothing. Both only can be found if they are transmitting.
| QUOTE (Jaid) |
| either way, stealth tags are not necessarily limited to signal 1 because of the limitations of regular RFIDs... |
They are not 'limited'. Every RFID tag has a signal of 1.
Of course, you could upgrade it...
| QUOTE (Rotbart van Dainig) | ||
Nothing. Both only can be found if they are transmitting. |
so in effect, going by the "locate hidden node" rules, a stealth tag is locatable, it will just have a high threshold...
except that stealth tags don't say they run on hidden mode, they just say they can't be found. which is kinda silly, to say the least, but whatever.
It will have exactly the same threashold as a commlink in that situation.
| QUOTE (Jaid @ May 11 2007, 07:14 PM) | ||
stealth tags generally have a signal rating of 6. it's right in the table, don't look at me and why wouldn't this give the benefit of networked comms cheops? you're just routing all your wireless traffic through the undetectable stealth tag. your PAN is still doing all the work, the stealth tags are just signal repeaters that transmit between the team. they get info from your PAN through a wire, and broadcast it to your teammate's stealth tags. the stealth tags that your teammates have will then transmit to your teammate's PAN by wired connection of some sort. your teammates then send info back through the same route, only reversed. |
Thanks I figured that all out while I was grocery shopping.
Stealth tags can't be detected like hidden nodes according to RAW.
Whether the tag has Signal 1 is only relevant if you are being jammed. Thanks to the mesh network it only has to be within range of a single device that is connected to the matrix to be able to talk to anything else that is within range of the matrix. And since stealth tags can't be detected...
Stealth Tag daisy chain to avoid broadcasting????
Amusing concept. I'll bite that stealthtags are 'undetectable' as written. I can even see how that works, they don't broadcast unless told.
Unfortunately for your idea, you just told them to start talking. Once they broadcast they are detectable. Now You'll want me to actually confirm that with rules...
Personally: I think RFID tags can't really work like this. Due to their 'microscopic' size I rather suspect they lack any real processing power, they are hard coded with whatever information they contain and that's it. The 'stealth tag' that only broadcasts when told to is going to be about as complex as they get.... and ironicaly, would probably be larger than non-stealth tags, while still being essentially invisible to the naked eye.
Now I just have to either find the right text to justify it, or the right lack of text to say 'you can't prove me wrong...'
Amusing concept. I'll bite that stealthtags are 'undetectable' as written. I can even see how that works, they don't broadcast unless told.
Unfortunately for your idea, you just told them to start talking. Once they broadcast they are detectable. Now You'll want me to actually confirm that with rules...
Personally: I think RFID tags can't really work like this. Due to their 'microscopic' size I rather suspect they lack any real processing power, they are hard coded with whatever information they contain and that's it. The 'stealth tag' that only broadcasts when told to is going to be about as complex as they get.... and ironicaly, would probably be larger than non-stealth tags, while still being essentially invisible to the naked eye.
Now I just have to either find the right text to justify it, or the right lack of text to say 'you can't prove me wrong...'
The most complex thing RFID tags can do is broadcast Sensor Information.
| QUOTE (Spike) |
| Personally: I think RFID tags can't really work like this. Due to their 'microscopic' size I rather suspect they lack any real processing power, they are hard coded with whatever information they contain and that's it. |
some RFID tags are hardcoded, some can be reprogrammed without physically opening them up. see the RFID tag entry for details
regardless, it's a moot point: the tag is not processing any data. it receives data (which i can't see a problem with) and transmits data (again, it doesn't look like you have a problem with that). the data is not changed in any way. no computation is required on the part of the stealth tag, that is all done in the PANs of the users.
But it doesn't offer any advantage from running in hidden mode - you are still braodcasting.
| QUOTE (Rotbart van Dainig) |
| But it doesn't offer any advantage from running in hidden mode - you are still braodcasting. |
it doesn't say anything about broadcasting or not. it just says it's undetectable.
| QUOTE (Jaid) | ||
some RFID tags are hardcoded, some can be reprogrammed without physically opening them up. see the RFID tag entry for details regardless, it's a moot point: the tag is not processing any data. it receives data (which i can't see a problem with) and transmits data (again, it doesn't look like you have a problem with that). the data is not changed in any way. no computation is required on the part of the stealth tag, that is all done in the PANs of the users. |
This debate is exactly why I assumed that you'd lose functionality in this method as compared to using commlinks. I assumed that tags were "dumb" and so had to be spoon fed all input.
It would work really well as a way of tagging one another so that your SG tells you not to shoot that person and so you know where the rest of the team is.
| QUOTE (Jaid @ May 12 2007, 12:21 AM) | ||
it doesn't say anything about broadcasting or not. it just says it's undetectable. |
No, it says 'cannot be located'. Which is in the context that one can determine the physical location of an RFID tag by using a comlink or signal scanner - and the fact that one can always read normal RFID tags... no test needed.
So there is not exactly a hard rule stating that one cannot detect the transmission of a stealth tag... just that they cannot be found as easy as normal tags.
On a side-note, most GM out there will give a good whipping with the bible to the player promoting such ideas.
I'm not so sure that located in this sense means physical location. I can't actually find the rules for the bug scanner but I seem to recall that it is basically a handheld Scan program. The Scan program lets you "locate" the signal but it doesn't triangulate its position (Track program, BBB 219). Anyone got the quote on bug scanners?
| QUOTE (Jaid @ May 11 2007, 03:02 PM) | ||
look a little closer... the column that starts off as "response" changes to "device rating" and the column that starts off as "signal" changes to "availability" about halfway down the table. it fooled me too, at first, until they pointed out the change |
oops missed that hahaha. and i was wrong, the pdf i have is 3rd print. ah well, i can always scan it in myself, as long as i dont give it to anyone its still legal right? not that i wouldnt get the real version when released, as i would like bookmarks and high quality.
| QUOTE (Rotbart van Dainig) |
| On a side-note, most GM out there will give a good whipping with the bible to the player promoting such ideas. |
whereas GMs who force their players to all take 50 points in electronics skills or to take no wireless signals anywhere are going to be oh so popular, i'm sure.
as far as i'm concerned, if the GM is declaring that runners must be either luddites or hackers, with nothing in between, because of what the rules say, then i'm gonna come right back at him and shove the rules in his face.
| QUOTE (Cheops) |
| I'm not so sure that located in this sense means physical location. I can't actually find the rules for the bug scanner but I seem to recall that it is basically a handheld Scan program. The Scan program lets you "locate" the signal but it doesn't triangulate its position (Track program, BBB 219). Anyone got the quote on bug scanners? |
| QUOTE (Wi-Fi Detection - pg 256) |
Many security networks—especially those monitored by spiders—automatically scan local wireless networks within range for signs of unusual activity. These networks will take note of new networks, perhaps even intercepting the signal to monitor or sniff out illicit activity. Security may even triangulate a network using multiple signals to determine of the network is originating from within its own boundaries. |
| QUOTE (Intercepting Wireless Signals - pg 225) |
Wireless traffic is broadcast through the air, so anyone within range of a signal can pick it up, whether they are connected to the transmitting party or not. |
If it broadcasts - it can be detected. Regardless of a flawed equipment entry or not.
Just my 2:nuyen:
ah, reprogrammable RFIDs 
i read about a person walking into a store that used RFIDs to id goods, and moved the id of something cheap onto a expensive bottle of wine using a handheld RFID RW-device
i read about a person walking into a store that used RFIDs to id goods, and moved the id of something cheap onto a expensive bottle of wine using a handheld RFID RW-device
| QUOTE (Jaid) | ||
whereas GMs who force their players to all take 50 points in electronics skills or to take no wireless signals anywhere are going to be oh so popular, i'm sure. |
As you may or may have not noticed, skills only matter at the scanning side.
So there is no point in your argument.
The only point is, that 'if it broadcasts, it can be detected'. Which holds true in both RL and RAW.
The rule concerning stealth tags is in the context of general RFID ruling... and the reason you cannot locate them is that they don't broadcast responses on general request.
| QUOTE (Jaid) |
| as far as i'm concerned, if the GM is declaring that runners must be either luddites or hackers, with nothing in between, because of what the rules say, then i'm gonna come right back at him and shove the rules in his face. |
So you intend to hardwire RFIDs (that aren't supposed to be hardwired) without the Hardware skill?
The whole setup is pure sillyness as you exchange on transmitter for another - and the latter isn't even intended to be connected in such a setup.
On the other hand, thank you for pointing out (again) that the origial premise of the thread (either luddite or ultra-hacker) is flawed.
Actually the argument he is stating makes sense. The OP basically said that it devolves to 2 extremes: Luddite or E-Warrior.
So if Stealth RFID tags don't transmit on general request and only transmit on a very specific passworded request, why can't hidden mode commlinks be treated in that fashion?
The BBB states they use special frequencies and "other tricks" to avoid detection and that they are encoded to remain silent. It also states that they can't be located with a commlink or bug scanner unless the codes are known. To me that means that unless the security spider can figure out the codes, then nothing in a 40m radius can locate it. Period. If we wanna go with the BBB stating that "almost every device is computerized and equipped with a wireless link" and be tools about that then we should at least consider that Stealth RFID tags cannot be found.
If an RFID tag can carry a super complex Olfactory Sensor Rating 6 (which can detect diseases by smell, continuously analyze the air for biological or chemical substances and pick up emotion scents) then I'm pretty sure it can handle being a router/transmitter.
So if Stealth RFID tags don't transmit on general request and only transmit on a very specific passworded request, why can't hidden mode commlinks be treated in that fashion?
The BBB states they use special frequencies and "other tricks" to avoid detection and that they are encoded to remain silent. It also states that they can't be located with a commlink or bug scanner unless the codes are known. To me that means that unless the security spider can figure out the codes, then nothing in a 40m radius can locate it. Period. If we wanna go with the BBB stating that "almost every device is computerized and equipped with a wireless link" and be tools about that then we should at least consider that Stealth RFID tags cannot be found.
If an RFID tag can carry a super complex Olfactory Sensor Rating 6 (which can detect diseases by smell, continuously analyze the air for biological or chemical substances and pick up emotion scents) then I'm pretty sure it can handle being a router/transmitter.
| QUOTE (WhiskeyMac) |
| Actually the argument he is stating makes sense. |
It doesn't - but let's get to that later.
| QUOTE (WhiskeyMac) |
| The OP basically said that it devolves to 2 extremes: Luddite or E-Warrior. |
Which is pretty much seen as nonsense, as you limit your options if you only go for extremes.
| QUOTE (WhiskeyMac) |
| So if Stealth RFID tags don't transmit on general request and only transmit on a very specific passworded request, why can't hidden mode commlinks be treated in that fashion? |
See, the exact same thing I'm saying, just the other way round - stealth tags broadcast in hidden mode.
| QUOTE (WhiskeyMac) |
| The BBB states they use special frequencies and "other tricks" to avoid detection and that they are encoded to remain silent. It also states that they can't be located with a commlink or bug scanner unless the codes are known. To me that means that unless the security spider can figure out the codes, then nothing in a 40m radius can locate it. |
That applies as long as the stealth tag isn't broadcasting... because that's the whole idea of such transponders.
| QUOTE (WhiskeyMac) |
| If we wanna go with the BBB stating that "almost every device is computerized and equipped with a wireless link" and be tools about that then we should at least consider that Stealth RFID tags cannot be found. |
No, 'we' shouldn't.
It's a can of worms, because, as you stated, a comlink would be perfectly able to mimic such behaviour.
Not to speak of the munchkin sillyness that by using s signal repeater, you can't be detected - because a rule take out of context seemingly says so.
| QUOTE (WhiskeyMac) |
| If an RFID tag can carry a super complex Olfactory Sensor Rating 6 (which can detect diseases by smell, continuously analyze the air for biological or chemical substances and pick up emotion scents) then I'm pretty sure it can handle being a router/transmitter. |
Most likely it can, but that's not the question.
The question is: How do you hardwire a cable to a tag that is smaller in diameter as said cable? (Hint: Get tags with Skinklink.)
| QUOTE (Rotbart van Dainig) |
| That applies as long as the stealth tag isn't broadcasting... because that's the whole idea of such transponders. |
i'm not sure that's 100% accurate. i haven't followed this thread closely, so maybe this has already been said, but assuming the stealth RFID tags are freq-hopping (and good god, why wouldn't they be?) and only transmitting sporadically, they really will be next to impossible to locate, realistically speaking. there's nothing to latch onto, no real pattern--every transmission is made on a hundred different frequencies, so there's no way to differentiate that transmission from random noise. theoretically, if the RFID tag isn't moving around, and you've got a few permanent receivers set up, you might eventually notice that there's random noise coming from the same spot over and over again. but it'd take weeks or months to accumulate enough data to even have a remote chance of accidentally stumbling on that.
now, if the stealth tag is transmitting constantly, then yeah, you'll probably notice it a lot faster. maybe even in a few hours, or even minutes if you've got a really paranoid security team that's expecting to find a tag.
Thing is, runners sharing their PANs are going to need to transmit data to each other a lot. A stealth tag, by contrast, doesn't transmit data except when prompted to by an appropriate code.
I see no reason why a runner's comm shouldn't be set to only transmit sporadically or not at all without the right stimulus (just like a stealth RFID tag). Of course, if there is no stimulus you have either limited or no access to the matrix or your team-mates, and lose any dice pool bonuses you might get from those connections.
My initial response to the OP still hasn't really been answered to my satisfaction. Sure, we can extrapolate the setting as we understand it to generate circumstances that we have to adopt the extremes of either luddite ninja or e-war specialist teams to work around, but why bother? What benefit does it bring us to say, for example, runner teams must avoid magic, and all take the murky link and magic resistance qualities because wards are ubiquitous and insurmountable and everyone is being followed by watcher spirits summoned by a great dragon? I exaggerate, but even so...
I see no reason why a runner's comm shouldn't be set to only transmit sporadically or not at all without the right stimulus (just like a stealth RFID tag). Of course, if there is no stimulus you have either limited or no access to the matrix or your team-mates, and lose any dice pool bonuses you might get from those connections.
My initial response to the OP still hasn't really been answered to my satisfaction. Sure, we can extrapolate the setting as we understand it to generate circumstances that we have to adopt the extremes of either luddite ninja or e-war specialist teams to work around, but why bother? What benefit does it bring us to say, for example, runner teams must avoid magic, and all take the murky link and magic resistance qualities because wards are ubiquitous and insurmountable and everyone is being followed by watcher spirits summoned by a great dragon? I exaggerate, but even so...
| QUOTE (mfb) |
| i'm not sure that's 100% accurate. |
The whole point is that any commlink can do the same.
Coming from a RL military background....
If it transmits "anything" it is detectable, frequency hopping or not. The frequency hopping is not over the entire EM spectrum. Frequency hopping merely makes the chances of the signal getting thru any interference, man made or not, better.
The only way they can be "undetectable" is of the tags not to transmit at all.
There is no reason why RFID tags and comms could not use "burst" transmission methods. Yes they could be detected, if but being in burst mode would make locating the transmitting device harder to locate.
Detecting a signal and locating a signal can be two different tasks.
With some over the counter equipment in todays tech, I can and have picked up frequency hopping signal devices and or devices/things interfering with frequency hopping devices. In some cases the signals were basically operating in a intermittent burst mode.
WearzManySkins
If it transmits "anything" it is detectable, frequency hopping or not. The frequency hopping is not over the entire EM spectrum. Frequency hopping merely makes the chances of the signal getting thru any interference, man made or not, better.
The only way they can be "undetectable" is of the tags not to transmit at all.
There is no reason why RFID tags and comms could not use "burst" transmission methods. Yes they could be detected, if but being in burst mode would make locating the transmitting device harder to locate.
Detecting a signal and locating a signal can be two different tasks.
With some over the counter equipment in todays tech, I can and have picked up frequency hopping signal devices and or devices/things interfering with frequency hopping devices. In some cases the signals were basically operating in a intermittent burst mode.
WearzManySkins
i dunno... if your commlink was to randomly transmit a brief burst of data every 1-2 seconds with random times in between (especially if the bursts are very quick) i don't see why you couldn't gain at least some benefits out of it. especially if you had some sort of program (high rating agent with some kind of autosoft and edit?) to sort through and estimate gaps 
| QUOTE (Rotbart van Daing) |
| The whole point is that any commlink can do the same. |
true, but not as well. a commlink isn't useful unless it's transmitting frequently, even if "frequently" only means "several times a minute". an RFID tag can go much longer between transmissions, and the transmissions can be extremely short. i guess there's no rules to simulate how often a network needs to transmit to work, so there's no rules effect. i'm not even sure if there should be, given SR's... interesting take on crypto.
| QUOTE (WearzManySkins) |
| With some over the counter equipment in todays tech, I can and have picked up frequency hopping signal devices and or devices/things interfering with frequency hopping devices. In some cases the signals were basically operating in a intermittent burst mode. |
yes, but were you operating in an environment where there are hundreds of thousands of transmitters within a one-klick radius, out of which massive amount of noise your job was to find "suspicious transmissions" without any more specific criteria?
| QUOTE (Jaid) |
| i dunno... if your commlink was to randomly transmit a brief burst of data every 1-2 seconds with random times in between (especially if the bursts are very quick) i don't see why you couldn't gain at least some benefits out of it. especially if you had some sort of program (high rating agent with some kind of autosoft and edit?) to sort through and estimate gaps |
ack, that would have the exact opposite effect. basically, the more often you transmit anything, even random static, the more chances you give the enemy of detecting you.
| QUOTE (mfb) | ||
true, but not as well. a commlink isn't useful unless it's transmitting frequently, even if "frequently" only means "several times a minute". an RFID tag can go much longer between transmissions, and the transmissions can be extremely short. i guess there's no rules to simulate how often a network needs to transmit to work, so there's no rules effect. |
And even the rules for detecting hidden mode don't specify such details.
okay then, plan C... buy a bunch of satellite links. at 500 nuyen each, you should be able to afford plenty.
now, put in ECCM 3. (they start off with device rating 3, and if you don't think a device with the sole purpose of signaling doesn't have the capacity to run a program to improve signal rating... well, you got problems)
they can now overwhelm any wifi inhibiting materials of rating less than 12. oddly enough, anything they bypass is completely ignored (i would personally have thought they would be reduced, but such is not the case).
long story short, if a four man team each buy 5 of these, and place them around the city, then that's now 20 signals going into all the supposedly wifi inhibited areas in the city, pretty much (technically, the GM can always introduce higher rating wifi inhibiting walls, but it's much cheaper to spam than it is to prevent it, i would say).
now then that's gonna generate some signal interference right there. have them move around, turn on/off randomly, etc for more fun... screw with everyone's security system.
now imagine that there could very well be regular people doing this sort of thing (probably not so much with the ECCM, mind you, but whatever). for every satellite link in a 100 km radius (including the satellites broadcasting back, mind you), that's gonna generate wireless signals in any place with less than rating 9 wifi inhibiting equipment.
conclusion: even supposedly wifi inhibited areas could easily be full of wireless traffic. all the runners need when they go in is to bring a transmitter that fills the entire inhibited area and a little bit outside, and that can penetrate the wireless inhibiting stuff. in order to determine if your signal originates from inside the facility or outside the facility, they now have to hack in... and i think it's safe to say that hacking into every single high strength signal is:
a) too time consuming
b) way too likely to backfire and result in them getting sued, fined, or otherwise penalised by the law
c) too resource intensive
so, there you go. problem solved. all it takes is 500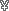 per satellite link, and a one-time investment of 1,500
per satellite link, and a one-time investment of 1,500 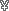 between the whole team, and you can render the wireless scan completely innefectual.
between the whole team, and you can render the wireless scan completely innefectual.
now, put in ECCM 3. (they start off with device rating 3, and if you don't think a device with the sole purpose of signaling doesn't have the capacity to run a program to improve signal rating... well, you got problems)
they can now overwhelm any wifi inhibiting materials of rating less than 12. oddly enough, anything they bypass is completely ignored (i would personally have thought they would be reduced, but such is not the case).
long story short, if a four man team each buy 5 of these, and place them around the city, then that's now 20 signals going into all the supposedly wifi inhibited areas in the city, pretty much (technically, the GM can always introduce higher rating wifi inhibiting walls, but it's much cheaper to spam than it is to prevent it, i would say).
now then that's gonna generate some signal interference right there. have them move around, turn on/off randomly, etc for more fun... screw with everyone's security system.
now imagine that there could very well be regular people doing this sort of thing (probably not so much with the ECCM, mind you, but whatever). for every satellite link in a 100 km radius (including the satellites broadcasting back, mind you), that's gonna generate wireless signals in any place with less than rating 9 wifi inhibiting equipment.
conclusion: even supposedly wifi inhibited areas could easily be full of wireless traffic. all the runners need when they go in is to bring a transmitter that fills the entire inhibited area and a little bit outside, and that can penetrate the wireless inhibiting stuff. in order to determine if your signal originates from inside the facility or outside the facility, they now have to hack in... and i think it's safe to say that hacking into every single high strength signal is:
a) too time consuming
b) way too likely to backfire and result in them getting sued, fined, or otherwise penalised by the law
c) too resource intensive
so, there you go. problem solved. all it takes is 500
Uh, a Sattelite Link has a Device Rating of 3, and thus a Signal Rating of 3.
Only the uplink has a Signal of 8.
Only the uplink has a Signal of 8.
| QUOTE (mfb) | ||
true, but not as well. a commlink isn't useful unless it's transmitting frequently, even if "frequently" only means "several times a minute". an RFID tag can go much longer between transmissions, and the transmissions can be extremely short. i guess there's no rules to simulate how often a network needs to transmit to work, so there's no rules effect. i'm not even sure if there should be, given SR's... interesting take on crypto. |
Given the seamless dynamic nature of the wireless Matrix and its 2-way full simsense capability, default timeouts of 1 centisecond or less would not be unreasonable.
| QUOTE (Rotbart van Dainig) |
| Uh, a Sattelite Link has a Device Rating of 3, and thus a Signal Rating of 3. Only the uplink has a Signal of 8. |
as you have pointed out earlier with respect to the stealth tags, specifics overrule the general rules. the satellite link has device rating 3, but if you read it's description it quite explicitly has a signal rating of 8, in and of itself, and is used for directly communicating with low orbit satellites.
| QUOTE (Jaid) | ||
as you have pointed out earlier with respect to the stealth tags, specifics overrule the general rules. the satellite link has device rating 3, but if you read it's description it quite explicitly has a signal rating of 8, in and of itself, and is used for directly communicating with low orbit satellites. |
Exactly what I said.
| QUOTE |
| This allows the user to uplink to communication satellites in low-Earth orbit, connecting to the Matrix from places where no local wireless networks exist. This link has a Signal rating of 8. |
So the uplink has a Singal of 8... and the repeater base station has a signal of 3.
| QUOTE (Rotbart van Dainig) | ||||||
Exactly what I said.
So the uplink has a Singal of 8... and the repeater base station has a signal of 3. |
there aren't 2 parts. there is one part. there is a satellite link, and that is all. the closest thing to a "second part" is the fragging satellite itself. the satellite link doesn't broadcast to a satellite uplink station which broadcasts to a satellite. the satellite link broadcasts to the satellite directly. it can explicitly be used when there is no wireless infrastructure around.
the satellite link *is* the part that has a signal of 8. it also has a response of 3, and can run ECCM 3 on it's system of 3, which will break through most any wifi inhibiting wallpaper around.
| QUOTE (Jaid) |
| there aren't 2 parts. there is one part. there is a satellite link, and that is all. |
Actually, no.
There are two connections:
The uplink and the ones of the device.
'This link' refers just to the 'uplink' part... the repeater base has a signal of 3.
Which is perfectly in conjunction with the Signal Rating Table.
| QUOTE (Rotbart van Dainig) | ||
Actually, no. There are two connections: The uplink and the ones of the device. 'This link' refers just to the 'uplink' part... the repeater base has a signal of 3. Which is perfectly in conjunction with the Signal Rating Table. |
what the heck are you talking about? it's one piece of equipment. there is no repeater base. there is nothing to even *imply* that there even *might* be a receiver base. it's *one* piece of equipment, with *one* set of stats.
your argument makes no sense. it's like i'm saying that a person has two ears, and you're saying that i'm wrong, it's actually his head that has two ears, and that his head is a completely separate entity from the rest of his body.
you're not making any kind of sense at all. would you care to explain where you get this repeater base nonsense from?
| QUOTE (Jaid @ May 12 2007, 06:38 PM) |
| what the heck are you talking about? it's one piece of equipment. there is no repeater base. there is nothing to even *imply* that there even *might* be a receiver base. it's *one* piece of equipment, with *one* set of stats. |
Not really.
It has two transceivers... one for the uplink - which is what 'This link' and Signal 8 refers to.
The other is the generic WiFi-enabledness, which comes at device rating 3, and thus, Signal 3.
At least, that's what the context of the description and the signal rating table tells us.
Wow, you really don't want to concede an inch. The satellite uplink is a satellite dish itself. It directly states that it allows a user to uplink to comm satellites in low-Earth orbit, creating wireless connectivity where no wireless networks exist. It doesn't go through a WiFi router, a repeater station, or other nonsense, it connects straight to the satellite through the portable satellite dish.
The Device Rating, which you say gets overridden based on specific stats, only applies to the Response, System and Firewall of the device because the Signal rating of the device is given as 8.
I just don't understand your argument. It seems like you're just being a rules lawyer for no other reason than to keep an argument going. There's no way that any self-respecting GM would be that much of an ass just so he can railroad you into having to play things his way or the highway.
The Device Rating, which you say gets overridden based on specific stats, only applies to the Response, System and Firewall of the device because the Signal rating of the device is given as 8.
I just don't understand your argument. It seems like you're just being a rules lawyer for no other reason than to keep an argument going. There's no way that any self-respecting GM would be that much of an ass just so he can railroad you into having to play things his way or the highway.
Let me explain, once again:
There is a thing piercing the sky, called uplink. That's got a Signal of 8.
That is what the description says.
Additionally, the whole device has a Device rating of 3... thus got a Signal of 3, to serve as a repeater on the ground.
Now... tell me... where's the railraoding in not having the repeating function of a portable sattelite dish a broadcasting power of surveillance radar?
There is a thing piercing the sky, called uplink. That's got a Signal of 8.
That is what the description says.
Additionally, the whole device has a Device rating of 3... thus got a Signal of 3, to serve as a repeater on the ground.
Now... tell me... where's the railraoding in not having the repeating function of a portable sattelite dish a broadcasting power of surveillance radar?
Let me try to clarify. A satellite uplink is useless by itself. Just try watching satellite television without a television. It doesn't work. The uplink must be connected to a comlink on the ground, somehow. If it isn't connected to your comlink then you can't actually do anything with it. Now, you could put the uplink on a motorized auto-targeting mount on a cyberlimb and wire it directly into your comlink, but that's just tacky. We can assume that the uplink acts as a wireless device and any comlink within range can connect to it. Rotbart van Dainig is suggesting that the signal is limited to 3 for this purpose.
Actually, if the dish itself has a signal of 8 then it simply doesn't work at all. According to the Signal Table in the BBB, a signal rating of 8 has a range of 100 kilometers. However, communications satellites orbit the earth at a little over 35,000 kilometers. If the dish has a signal rating of 8 then it cannot possibly communicate with any communications satellite. Period. End of sentence.
(One should note that the description says Low Earth Orbit, which communication satellites never use because they move to fast to maintain a good signal. However, LEO begins at 200km, still well outside of the signal range of the satellite link, and ends at 2000km.)
For this reason, it is highly unlikely that the signal of 8 refers to the connection between the satellite link and the satellite. It would require a signal in excess of 9 to to reach a communications satellite. If the pattern on the signal table repeats itself, it would need a signal of 13, in fact. If they are going to stick with LEO despite the difficulty of tracking a satellite at that orbit then a signal of 11 would be necessary to cover the entire spectrum.
Actually, if the dish itself has a signal of 8 then it simply doesn't work at all. According to the Signal Table in the BBB, a signal rating of 8 has a range of 100 kilometers. However, communications satellites orbit the earth at a little over 35,000 kilometers. If the dish has a signal rating of 8 then it cannot possibly communicate with any communications satellite. Period. End of sentence.
(One should note that the description says Low Earth Orbit, which communication satellites never use because they move to fast to maintain a good signal. However, LEO begins at 200km, still well outside of the signal range of the satellite link, and ends at 2000km.)
For this reason, it is highly unlikely that the signal of 8 refers to the connection between the satellite link and the satellite. It would require a signal in excess of 9 to to reach a communications satellite. If the pattern on the signal table repeats itself, it would need a signal of 13, in fact. If they are going to stick with LEO despite the difficulty of tracking a satellite at that orbit then a signal of 11 would be necessary to cover the entire spectrum.
| QUOTE (hyzmarca) |
| Actually, if the dish itself has a signal of 8 then it simply doesn't work at all. According to the Signal Table in the BBB, a signal rating of 8 has a range of 100 kilometers. However, communications satellites orbit the earth at a little over 35,000 kilometers. If the dish has a signal rating of 8 then it cannot possibly communicate with any communications satellite. |
Sssh. That would require gear to make technical sense, and stuff.
Perhaps we'll see rules in unwired for the range of directional signals... with a +50%, it might work.
| QUOTE (hyzmarca) |
| For this reason, it is highly unlikely that the signal of 8 refers to the connection between the satellite link and the satellite. |
Actually, it would in either case, per RAW. Either it's just the uplink, or its both the uplink and the repeater station. But the max Signal Rating stays 8...
But, anyway, Signal 8 is the broadcasting strength for flight/ground RADAR.
And we all know RADAR causes cancer.
You don't want cancer, do you, Jaid?
| QUOTE (Rotbart van Dainig) |
| But, anyway, Signal 8 is the broadcasting strength for flight/ground RADAR. And we all know RADAR causes cancer. You don't want cancer, do you, Jaid? |
cancer sounds good. i'll just wait for arsenal to come out and then turn myself into a cyborg, and we'll see who's laughing then (note: past editions would seem to suggest that touching cyberlimbs with a 20 foot pole is not a good idea, so it may very well be you
regardless, it doesn't say anything about 2 separate parts. it just says it has signal 8. you can make up stuff if you like, but it's still just made up stuff.
| QUOTE (Jaid @ May 12 2007, 08:44 PM) |
| regardless, it doesn't say anything about 2 separate parts. it just says it has signal 8. you can make up stuff if you like, but it's still just made up stuff. |
Indeed, it doesn't tells us that there are two parts.
It just tells us that there it creates an uplink to a satellite and that this link has a Signal of 8.
Of course, this doesn't work, no matter how you put it, but then again, most of the cheap comlinks won't really work, either.
| QUOTE (mfb) |
| i'm not sure that's 100% accurate. i haven't followed this thread closely, so maybe this has already been said, but assuming the stealth RFID tags are freq-hopping (and good god, why wouldn't they be?) and only transmitting sporadically, they really will be next to impossible to locate, realistically speaking. there's nothing to latch onto, no real pattern--every transmission is made on a hundred different frequencies, so there's no way to differentiate that transmission from random noise. theoretically, if the RFID tag isn't moving around, and you've got a few permanent receivers set up, you might eventually notice that there's random noise coming from the same spot over and over again. but it'd take weeks or months to accumulate enough data to even have a remote chance of accidentally stumbling on that. now, if the stealth tag is transmitting constantly, then yeah, you'll probably notice it a lot faster. maybe even in a few hours, or even minutes if you've got a really paranoid security team that's expecting to find a tag. |
Well, the whole concept of RFID tags was not understood by the person writing the book. As generally used, they are passive until excited by a scanner. They have a range of maybe 10-20 meters if you do silly things to increase the range of the scanner for odd purposes, it's more typically a few meters.
The reason they are really hard to detect is that they are totally inert without the scanner exciting them. They have no power supply, they get powered by the scanner.
There are rfid that have a internal battery, and can potentially transmitt all the time.
| QUOTE (hobgoblin) |
| There are rfid that have a internal battery, and can potentially transmitt all the time. |
Yes and those RFID are not as small as the non battery powered ones, and if they transmit all the time, the battery life is in days at best.
WearzManySkins
Well, when have battery life ever been tracked in a sr version?
| QUOTE (hobgoblin) |
| Well, when have battery life ever been tracked in a sr version? |
Sigh, yes so true, but very true.
Ok they are not as small.
| QUOTE (hobgoblin) |
| Well, when have battery life ever been tracked in a sr version? |
When you're dealing with stun weaponry.
This is a "lo-fi" version of our main content. To view the full version with more information, formatting and images, please click here.