Since the release of SR4 I have been pondering and debating the role of wireless communications and the average shadowrunner. This may not apply to you if you let your runners 'have fun', but if you are trying for a gritty 'realistic' approach to Shadowrunning, then this could be a valuable topic.
Note: This entire discussion will not handle the role of magic. In some cases the mage is identical to the E-war specialist, in some ways not. His presence can trip alarms that mundanes would breeze through, but he can do things his mundane counterparts can only dream of. There are significant differences, but they are beyond the scope of this discussion.
The writers of the MRB make one common error. They assume that the ubiquity of an item/phenomenon in the dominant culture must have a corresponding impact in the criminal subcultures.
This is prevelant across multiple spectrums. This is why you see images of Shadowrunners wearing loud colors, or 'action movie violence' in almost every tale told of almost any run. This leads to the culture of 'Shadowrunners' who live their lives 'on the job'. They hang out with other shadowrunners, use only their handles and hang out on popular, well known 'shadow havens'.
And they carry their commlinks on every job.
I'm not going to address every issue, just that last one.
In the default mode, Shadowrunners go on the job with a commlink set to hidden mode, every man jack of them, their PANs swapping data left and right, and maybe the hacker running a little C&C for them, pulling down additional tactical data from the security net.... if he's not busy swagging pay-data in the middle of the firefight.
Sound good, right?
Actually its the worst way to run. You have one guy who MIGHT be watching to see that your network isn't infiltrated and corrupted. You leave data trails all over the place, and any half competent security team will know the moment you go where you aren't supposed to. Lets look at why before we cover the alternatives.
First of all, one hacker, even two hackers are going to be busy with other tasks. Tasks like trying to sweep up the data trail the runners leave. Security hackers can act much like snipers, waiting in ambush for the right moment to reveal their hand. A hidden network is far from 'invisible'. It's a protocol, not magic, and the MRB shows that security drones and teams are very capable of detecting a Hidden Network's existance. Breaking and entering for the sec teams will start with the weakest links, the muscle and the mages. Once they've infiltrated one commlink they can monitor every movement, every action, every bit of data that the entire network shares from that one commlink.
The other aspect is the ease of detection. See, unlike the public street, corporate offices are 'closed environments'. Patrolling guards, even drones are increasingly rare due to cost/benefit analysis. They'll never completly go away, a visible guard being necessary for human psychology, but they aren't really there to stop anyone determined to go in. Security however will map every node, every WiFi chair, coffee machine and door. Even spoofing will only cover so much when it only takes one node out of a thousand to go 'hey! There's a signal here where there shouldn't be'... and make no mistake, there will be a signal. You can't have electronic communication without it. Even ONE RFID tag will give the team away in a hot second to any half competent security system...
And that's just the quick overview of the flaws.
There are two solutions. One is simple, requires almost no skill or work, but is at the same time incredibly limiting. The other is the exact opposite.
The simple solution, the one many pro's will use, and many wannabe pro's might chose to emulate, is cheap and simple. It does require altering your mindset, however.
Go clean. Scrub every item, make sure you have no nodes, no RFID tags, nothing. Only designated team members carry commlinks, and those are in the 'Off position'. Smarter teams will buy commlinks and programs specifically for that run and dispose of them the moment they don't need them, preferabbly with thermite.
In the Wireless World, these guys are ninjas. With increasing use of 'reality filters' there is a good chance a significant percentage of the population on a crowded street can't even SEE them, they don't exist. Security teams, reliant as they are on electronic detection will be ignorant of their existance. Good old fashioned stealth techniques are still necessary, perhaps even more important as they can't rely on their hacker to spoof more conventional sensors for them.
On that note, many security devices, particularly older devices (more than ten years old) and in 'High Security Areas' are probably hardwired, making them immune to conventional wireless spoofing. Newer, cheaper, security setups are less predictable (as the sensors can be moved around regularly) but are vulnerable to hackers.
It is easier to go clean that the MRB would suggest. Off the shelf clothes will naturally have more options, but I doubt handicrafts have gone completely away, and there will still be people making their own. Guns have a very long shelf life, and in many cases the gun-owners can be sold 'traditional' guns at higher costs. Traditional guns lack the bells and whistles... like nodes. They may still be tagged, but tags can be detected and 'burned' relatively simply.
More to the point, as many 'pros' will use Clean techniques, the gear available for sale through select sources may even brag about how it lacks extranious electronics. Merchants might even cater to certain crowds of 'extremists' who like to 'get away' from it all.
The Luddite Ninja team is not limited to 'low tech' either. Hackers can turn on commlinks when necessary, or once the 'shit has hit the fan' to function in an 'E-War' capacity. Drones with solid pilot software can remain outside the 'job site' until called in as 'cavalry', either by a signal sent from the hacker or if their wireless has been deliberately disabled then by a visual signal such as a flare. If you are calling in the drones, then stealth is no longer an option.
The weaknesses are manifold and obvious. Loss of solid communications, loss of any PAN bonuses the GM might give out, loss of spoofing and on the fly hacking of security systems. Everything must be dealt with physically or not at all. Against older security systems the Luddite Ninja's actually will have a harder time of it, as there will be more physical sensors than electronic, and the Hacker typically won't be trying to subvert the security central.
On the other hand, in addition to being 'Ghosts' they are immune to the Security teams most valuable members, the E-War specialists. In theory a team of Adepts and mages is more effective at 'Luddite Ninja' work than conventional cybered operatives, but this not generally proven in actual use. Cyber/bioware can easily be rendered 'wireless' in most cases, and should by any runner with a sense of self preservation.
The other option is to ensure that as many members of the team are fully kitted out electronic warfare specialists as possible. This team requires more brains than brawn, and their commlinks and associated skills are even more important than their ability to fire a gun.
The Goal of the E-War commando isn't to fly below the radar, it's to fucking OWN that radar and anyone who ever touched it. They aren't quiet, no they are like the earthquake, where everything around you moves so in sync that you are almost fooled into thinking that nothing is moving at all. E-War teams will have two or three guys just neutralizing the security network, subverting it, paralysing the enemy by shutting down their every move before they can make it. Drones will be flying shotgun, and any node that looks even remotely useful will be subverted at the earliest convienence.
All this is not unusual, however. Where the E-war team really earns it's money is when they don't get eveything fully locked down, when security finally mobilizes it's high threat response teams, their drones and jammers and so forth.
E-War teams dominate electronic combat. Sec teams never run 'clean'. Defenders try to use every advantage in their favor, and stealth isn't important. A good sec team has one or more E-War spec's of their own, guys who's job it is to own the attacker's network, to jam their comms and otherwise monkey-wrench the Runners.
The E-War team is in an armsrace against these guys, and they brought the biggest guns they could get. Cyberware get's spoofed, IFF tags change from freind to 'foe'. The loser in such a battle winds up doing more harm to his own side than the enemy.
That said, its probable that even the E-War guys don't use drones that rely on wireless communications. It's a vulnerability they can't afford. Security has to monitor their drones, it's a liabilty issue and a security issue. An attack team can't afford to let their assets be left vulnerable to a hack. E-war teams probably run multiple overlapping networks, so that a loss of any network security (or network specific jamming) doesn't cripple them.
Sorry if I've abbreviated the e-war team, but I will come back to it if necessary.
Full Version: Luddite Ninja Shadowrunners Vs. E-War Commando's
I don't fully understand your point. Gritty or not, it's a game, and what is 'realistic' is determined by the GM.
As written, spoofing your data trail is a reasonably simple activity, and it is not unreasonable to suggest that in amongst all the other wireless noise, a team of runners might still communicate without being noticed.
If you wish to ditch 2 archetypes for your ninja luddite team or require 2 hackers for every other team member as in your E-war commando team, go to it. But interesting as your discourse is, it seems to lack a point.
As written, spoofing your data trail is a reasonably simple activity, and it is not unreasonable to suggest that in amongst all the other wireless noise, a team of runners might still communicate without being noticed.
If you wish to ditch 2 archetypes for your ninja luddite team or require 2 hackers for every other team member as in your E-war commando team, go to it. But interesting as your discourse is, it seems to lack a point.
interesting take. to comment on the applicability of these ideas, i think there's room in SR for all three styles of running--the standard way presented in the book, the luddite ninja way, and the e-shock-and-awe way. most runners go with the standard way, because it's the easiest. they depend on getting in and out fast enough that their sloppy e-habits don't get them in much trouble, and they depend on the generally sloppy e-habits of their fellow runners to protect them from being singled out. shadow ops are rampant, in the sixth world, and corps don't generally want to waste time and resources chasing down spillers of milk--they're more interested in cleaning up the mess. occasionally, a runner team will get well and truly screwed by their sloppy e-habits, but that's only to be expected. most runners think it will never happen to them--and most runners are right.
it's only when you get into the high-class runners that you start seeing luddite ninjas. these guys are canny and smart. they've realized that while swimming in the school with the rest of the fish is PGP against sharks, it's much safer to not be seen at all. you might also see a few green operators--Salish-Sidhe strike teams, for instance--go with the luddite ninja concept.
runners, in general, don't do the e-shock-and-awe thing. they're not good enough, and they don't have the support necessary. if you're that good, there's really no reason to keep running the shadows--somewhere, somebody will hire you, pay you a much higher wage than you can make hustling jobs, and ignore or even bury whatever sins you've committed that put you out on the street in the first place. Ghosts, Wildcats, and the like go in for e-shock-and-awe, because they can afford to and because it's the best way to do it.
it's only when you get into the high-class runners that you start seeing luddite ninjas. these guys are canny and smart. they've realized that while swimming in the school with the rest of the fish is PGP against sharks, it's much safer to not be seen at all. you might also see a few green operators--Salish-Sidhe strike teams, for instance--go with the luddite ninja concept.
runners, in general, don't do the e-shock-and-awe thing. they're not good enough, and they don't have the support necessary. if you're that good, there's really no reason to keep running the shadows--somewhere, somebody will hire you, pay you a much higher wage than you can make hustling jobs, and ignore or even bury whatever sins you've committed that put you out on the street in the first place. Ghosts, Wildcats, and the like go in for e-shock-and-awe, because they can afford to and because it's the best way to do it.
That's some good points too, mfb. I don't think the bar for entry is so high necessarily for shock and awe tactics, or that shadowrunners are necessarily restricted to 'money grubbing' either, but certainly there is some heavy requirements to get a team of E-War ops together and fully equipped.
On that, I see Shadowrunners filling a spectrum... your grim and dirty street punks on up to elite 'world class' mercs who get millions per run, and probably spend most of it keeping in the very top ranks.
On that, I see Shadowrunners filling a spectrum... your grim and dirty street punks on up to elite 'world class' mercs who get millions per run, and probably spend most of it keeping in the very top ranks.
They sure as hell will, if they burn everything that could even remotely compromise after a job... even more as that includes burning their entire body and getting a new cyborg one.
Those ideas are fancy and all, but hardly something people can reliably pull.
Basically, everything is a tradeoff, and the point is to maintain the balance of cost and return.
Those ideas are fancy and all, but hardly something people can reliably pull.
Basically, everything is a tradeoff, and the point is to maintain the balance of cost and return.
My current group is DEFINITELY an E-Warrior squad, and yeah, we're about as subtle as Godzilla on a PCP bender. 5 man team, consisting of a combat hacker, Mage, Technomancer, Face and a Hacker/Drone rigger. Both the mage (me) and the Face also have a couple points of Computer skill and SkillWire systems dedicated to approximating the Cracking Skill group and some pretty hefty commlinks suped up courtesy of the Hacker/Rigger. Honestly though, me and the face's commlinks are mostly there to provide extra horsepower to run Agents and drones without straining the real professional's response any. The way we operate is pretty simple, although it probably depends a bit more on the Technomancer than many people would be comfortable with (yes, that's right, the TM). Basically, the TM brute forces and makes the network ours, after which the rest of us drops some Agents, and generally run interference so the TM doesn't have to risk Fading/Damage or use Sprite services until his sheer power becomes necessary, at which point he and the Hacker/Rigger promptly boots opposing forces off the 'trix. Still, I must admit, things get pretty hairy if we're stuck trying to multi-task the 'trix work and physical operations too much simultaneously; we're dangerously dependent on spirits and stolen drones for muscle, and pretty weak in terms of traditional stealth. So far, it's mostly been a theoretical weakness, but if and when we lose the 'trix war, my group will be pretty well boned. It's been fun so far, but I can see how it wouldn't be feasible for a group that doesn't really plan their whole team together. BP wise though, it's not really that expensive as long as you have a hacker or two who can copy/pirate a few high end vital programs. Umm, that and somebody has to take one for the team and be a TM with the physical constitution of wet tissue paper.
...ahh this makes me long for the good old pre-wireless days of shadowrunning.
| QUOTE (Kyoto Kid) |
| ...ahh this makes me long for the good old pre-wireless days of shadowrunning. |
complete with npc deckers?
| QUOTE (hobgoblin) | ||
complete with npc deckers? |
...small price to pay for being able to run in truly SINless style...
Actually, I did have two decker PCs: Diamond IC and the original Violet. Even figured out how to build a cyberdeck and create programmes from scratch.
| QUOTE (hobgoblin) | ||
complete with npc deckers? |
And the comm systems that cost
...yeah, but you also could start with up to 1 mil in resources, 2 mil if you used the MR J's LBB advanced chargen rules.
Still excessive when you think about how much a walkie talkie costs...
...I agree, some of the costs in SR3 were out of line (like Fake IDs) This doesn't prevent a GM from modifying them If he/she feels they are too out of line.
It's just that things felt so much more "Shadowrun" before the crash.
It's just that things felt so much more "Shadowrun" before the crash.
and how does it feel now?
btw, this looks strangely like the threads about CPv3 over on vfte forum...
oh, and this thread is officially derailed
btw, this looks strangely like the threads about CPv3 over on vfte forum...
oh, and this thread is officially derailed
My question is simple:
Given the RAW and with as little GM house rules as possible, which style of running is mathematically the easiest? Then that is the style that is by default the most probable style.
Given the RAW and with as little GM house rules as possible, which style of running is mathematically the easiest? Then that is the style that is by default the most probable style.
Don't forget how easy it is to spoof your RFID and comlink sig... "So you're saying that Bucktusk Bertha, the infamous Troll hooker of many a sorrid street tale, crept past you guys, dropped a Hiroshima-sized e-bomb on our servers and crept back out without a single trace...all 2.7m and 300 kg of her...with that limp..."
I would imagine that there is a fairly strong network of hackers just surfing the streets looking for some chump who is too cheap to buy a decent comlink/OS combo so they can do a run with their ID. I can tell you that CorpSec would start getting pretty frustrated the 15th time they raided a BTL-whore or pizza delivery boys conapt looking for the Shadowrunner team that took out their last chipset shipment while it was en-route down I-5.
Not that I've ever done this myself...
Mark(psycho)Phipps( HAHAHA! )
I would imagine that there is a fairly strong network of hackers just surfing the streets looking for some chump who is too cheap to buy a decent comlink/OS combo so they can do a run with their ID. I can tell you that CorpSec would start getting pretty frustrated the 15th time they raided a BTL-whore or pizza delivery boys conapt looking for the Shadowrunner team that took out their last chipset shipment while it was en-route down I-5.
Not that I've ever done this myself...
Mark(psycho)Phipps( HAHAHA! )
| QUOTE (psychophipps) |
| Don't forget how easy it is to spoof your RFID and comlink sig... "So you're saying that Bucktusk Bertha, the infamous Troll hooker of many a sorrid street tale, crept past you guys, dropped a Hiroshima-sized e-bomb on our servers and crept back out without a single trace...all 2.7m and 300 kg of her...with that limp..." I would imagine that there is a fairly strong network of hackers just surfing the streets looking for some chump who is too cheap to buy a decent comlink/OS combo so they can do a run with their ID. I can tell you that CorpSec would start getting pretty frustrated the 15th time they raided a BTL-whore or pizza delivery boys conapt looking for the Shadowrunner team that took out their last chipset shipment while it was en-route down I-5. Not that I've ever done this myself... Mark(psycho)Phipps( HAHAHA! ) |
/Agree
In fact I see low-level pay-data being exactly this.
Hacker moonlights for 'chump' IDs.
Begining hackers get jobs waiting in malls and scanning / compromising IDs to sell to fixers to provide short use IDs for runs.
Hell, take it a step further. Use a fly-ass honeypot elf contact to get in the targets pants and get the goods that way. Nothing says 'successful shadowrun' like hearing the building's LAN ask you, "Would you like to see who's on guard duty tonight, Mr. Tolliver?" right as you walk through the back door.
Mark(psycho)Phipps( HAHAHA! )
Mark(psycho)Phipps( HAHAHA! )
I'm with mfb. I don't really see how the rulebook doesn't accept those various styles, but instead what style a runner team uses will depend on the runner team and the job.
| QUOTE (toturi) |
| My question is simple: Given the RAW and with as little GM house rules as possible, which style of running is mathematically the easiest? Then that is the style that is by default the most probable style. |
that depends on the enviroment, which is entirely GM-dependant.
Spike! 
I really like this take on things. Ive been missing the nitty gritty shadowrun reality ever since SR3 was tossed out. I think this gives the new wireless proliferation some balance.
This is some of the best realistic thinking Ive seen in a while, keep it up.
I really like this take on things. Ive been missing the nitty gritty shadowrun reality ever since SR3 was tossed out. I think this gives the new wireless proliferation some balance.
This is some of the best realistic thinking Ive seen in a while, keep it up.
| QUOTE (Fix-it) | ||
that depends on the enviroment, which is entirely GM-dependant. |
Not entirely. The environment may be GM controlled but how the environment actually reacts in terms of game mechanics shouldn't change. The GM may decide in favor of certain responses, but (without house ruling) how the responses deal with the hacker should mechanically be about the same.
| QUOTE (psychophipps) |
| Don't forget how easy it is to spoof your RFID and comlink sig... "So you're saying that Bucktusk Bertha, the infamous Troll hooker of many a sorrid street tale, crept past you guys, dropped a Hiroshima-sized e-bomb on our servers and crept back out without a single trace...all 2.7m and 300 kg of her...with that limp..." |
i think the issue is that some here on the forum have the mindset that any comlink signal after hours would have every piece of available security thrown at it .0001 second after detection.
how, having a signal generator smuggled in that will transmit a signal at semi random intervals after office hours would be interesting
cry wolf enough times and no-one will care as its most likely a glitch. that is as long as they don't find said generator...
In my experience, going E-War is easier, but has higher minimum requirements. Not all groups are going to have enough players to do it and still have a semblance of a balanced team, after all, and even then you're assuming that even the non-hackers are willing to divert some resources to being able to at least have beefy commlinks and Agent programs.
| QUOTE (hobgoblin) |
| and how does it feel now? |
...kind of like how some reality shows make me feel. Or maybe like Today's NASCAR compared to the days when they actually raced stock cars.
Since this is completely related to the other thread about Wi-Fi detection let me bring up another point.
How do you handle Infiltration? Do the guards continuously search for infiltrators, thereby making it an Int + Per (15+, 1 CT) check or do you only give the guards a single opposed Int + Per (Agi + Inf) test?
Walking into the lobby and saying "hello fraggers!" to the guards = Active comm
Walking into the lobby, head down and saying nothing = Passive comm
Sneaking into the lobby, behind the shrub, under the counter = Hidden comm
1st situation: guards know you are there = you add yourself to their lists
2nd situation: guards know you are there = you are listed but don't ask for access
3rd situation: guards make Int+Per (Agi+Inf) = EW + Scan (4)
If you prefer to play all your games where as soon as you step onto corporate territory and everyone makes extended detection tests against you then you have to apply it to all "levels" of reality equally.
This means that security should be making:
Intuition + Perception (15+, 1 CT) and physically find you in about 3 mins
EW + Scan (15+, 1 CT) and find you on the matrix in about 3 mins
Intuition + Assessing (15+, 1 CT) and find you astrally and physically in about 3 mins
That doesn't sound fun to me.
How do you handle Infiltration? Do the guards continuously search for infiltrators, thereby making it an Int + Per (15+, 1 CT) check or do you only give the guards a single opposed Int + Per (Agi + Inf) test?
Walking into the lobby and saying "hello fraggers!" to the guards = Active comm
Walking into the lobby, head down and saying nothing = Passive comm
Sneaking into the lobby, behind the shrub, under the counter = Hidden comm
1st situation: guards know you are there = you add yourself to their lists
2nd situation: guards know you are there = you are listed but don't ask for access
3rd situation: guards make Int+Per (Agi+Inf) = EW + Scan (4)
If you prefer to play all your games where as soon as you step onto corporate territory and everyone makes extended detection tests against you then you have to apply it to all "levels" of reality equally.
This means that security should be making:
Intuition + Perception (15+, 1 CT) and physically find you in about 3 mins
EW + Scan (15+, 1 CT) and find you on the matrix in about 3 mins
Intuition + Assessing (15+, 1 CT) and find you astrally and physically in about 3 mins
That doesn't sound fun to me.
| QUOTE (hobgoblin @ May 10 2007, 08:34 AM) |
| i think the issue is that some here on the forum have the mindset that any comlink signal after hours would have every piece of available security thrown at it .0001 second after detection. how, having a signal generator smuggled in that will transmit a signal at semi random intervals after office hours would be interesting cry wolf enough times and no-one will care as its most likely a glitch. that is as long as they don't find said generator... |
Great point. What happens if an exec grabs a new earpiece for his comlink? Or the new upgrade has a small glitch about Novalogic MP3 players? There is a certain amount of traffic in general areas that is to be expected without sending in the big black-clad trolls with big black shotguns. If they responded to every stray signal they'd soon go crazy with them.
Of course, the data vault is another thing entirely...
Mark(psycho)Phipps( HAHAHA! )
| QUOTE (psychophipps) | ||
Great point. What happens if an exec grabs a new earpiece for his comlink? Or the new upgrade has a small glitch about Novalogic MP3 players? There is a certain amount of traffic in general areas that is to be expected without sending in the big black-clad trolls with big black shotguns. If they responded to every stray signal they'd soon go crazy with them. Of course, the data vault is another thing entirely... Mark(psycho)Phipps( HAHAHA! ) |
well i talked about after hours, when the office should be deserted...
and if not, the person still present should still show up as signed in and all that.
hell, comlinks are supposed to work as id's so...
Obviously Luddite Ninjas are mathamatically simpler. The entire point is that they skip out on a huge chunk of rules/security from the get go. The E-War Commandos simply move the bulk of their dice rolling from combat to E-Combat, which is a good route to go if everyone knows the ins and outs of the Wireless chapter but keeps forgetting how to implement called shots, say.
Realistically, security would be scanning for analomous networks all the time. Remember it's not 'security' in the form of some chump checking a monitor but a series of 'single purpose' sensors running dedicated software that you really have to watch for.
The chair/coffee machine thing is a 'secondary network', slower, less effective, but provides a good backup.
Computers don't get tired, they don't take piss breaks and they absolutely excell at repetetive tasks (every 3 milleseconds scan for networks. If one is detected check it against a list. If it's on the list ignore it, if it's not, move on to step four...) The better the system the faster and more effectively it will be able to report that Mr. Smith shouldn't be in the office at this hour, or whatever.
E-War/hackers would be 'spoofing' the system by making sure their network is 'authorized', that is 'on the list'.
The key, mechanically, is to run it so that networks are 'detected' more or less automatically once they are in range of a sensor. If you really want to use the rules for 'detecting' a hidden network... really just finding it amongst background noise (other networks) you run it as an extended test every 'round', as the computer exhaustively runs through every signal it finds to check it for authorization. The extended test becomes your 'timelimit' to successfully present yourself as authorized or otherwise circumvent the system.
ALL of this more or less assumes that the Runners are going in 'after hours'. While the same general rules apply to duty hours, the proliferation of 'other signals' make is more practical to run a more conventional Op. The goal during 'duty hours' is to blend in. Reality filters are not so prevelant, or so total, that luddite ninja's won't be fully visible to ordinary people. E-War types will still have to blend physically into their environment as well, and running 'hot' is going to make them stand out as fully as the guy with no commlink at all...
Realistically, security would be scanning for analomous networks all the time. Remember it's not 'security' in the form of some chump checking a monitor but a series of 'single purpose' sensors running dedicated software that you really have to watch for.
The chair/coffee machine thing is a 'secondary network', slower, less effective, but provides a good backup.
Computers don't get tired, they don't take piss breaks and they absolutely excell at repetetive tasks (every 3 milleseconds scan for networks. If one is detected check it against a list. If it's on the list ignore it, if it's not, move on to step four...) The better the system the faster and more effectively it will be able to report that Mr. Smith shouldn't be in the office at this hour, or whatever.
E-War/hackers would be 'spoofing' the system by making sure their network is 'authorized', that is 'on the list'.
The key, mechanically, is to run it so that networks are 'detected' more or less automatically once they are in range of a sensor. If you really want to use the rules for 'detecting' a hidden network... really just finding it amongst background noise (other networks) you run it as an extended test every 'round', as the computer exhaustively runs through every signal it finds to check it for authorization. The extended test becomes your 'timelimit' to successfully present yourself as authorized or otherwise circumvent the system.
ALL of this more or less assumes that the Runners are going in 'after hours'. While the same general rules apply to duty hours, the proliferation of 'other signals' make is more practical to run a more conventional Op. The goal during 'duty hours' is to blend in. Reality filters are not so prevelant, or so total, that luddite ninja's won't be fully visible to ordinary people. E-War types will still have to blend physically into their environment as well, and running 'hot' is going to make them stand out as fully as the guy with no commlink at all...
It also depends on where the 'run is happening. Yeah, the corp tower will have all these goodies in non-public areas but that warehouse down by the docks with 10,000+ sq ft, constant damp, heavy machinery and the disruptive electrical fields from that machinery? Not so likely.
By the time your team runs something like what's being discussed here, they're either in the Top 100 or an unwitting distraction so the real team doing the run can do the job on the down-low since Corp-Sec is "busy" at the moment...
Mark(psycho)Phipps( HAHAHA! )
By the time your team runs something like what's being discussed here, they're either in the Top 100 or an unwitting distraction so the real team doing the run can do the job on the down-low since Corp-Sec is "busy" at the moment...
Mark(psycho)Phipps( HAHAHA! )
Well, it might be a bit silly to go 'LN' or 'E-W' on a hit of a Stuffer Shack, but given the wide spread existance of cheap computing and wireless sensors, those talents are not completely wasted either...
...you just have a lot more slack to fuck up in.
In your warehouse senario, every crate is tagged eight ways to sunday, if only for inventory management, but the inside is probably as light sec as you get. There simply isn't any 'infrastructure' to actually support that level of security.
This sort of stuff, security wise anyway, is really more limited to AAA R&D labs, HQ's and delta level labs. You'll find similar setups in government offices, if for less reason now.
Of course even AA corps probably use similar setups, sec wise, they just have less budget for HRT teams and the like. At that point you are dealing with third party security that gets called in, easier to cut the signal to the security provider, isolating the target. Human On-site security, at that point, would lock themselves in their offices until the threat went away. Of course, you can always get some young hotshot out to get himself killed.
The issue I have with the Wireless world, if I really wanted to take umbrage at anything, was just how easy Spoofing your datatrail supposedly is. At best all you can do is eliminate the surface trail, make them dig to actually track you down. Spoofing would practically leave a trail of it's own, the actual focus should be on why corps don't root out shadowrunners (because it takes long enough that it becomes an exercise in vengance, nothing more. And vengance isn't cost effective...).
The way I'd use this, btw, is simple. Let the players encounter, on an otherwise ordinary Run against an only sorta-hard target, run into a sec team with two E-War guys in it. The first time their PAN's get turned against them they'll figure out their own way to avoid it in the future, and it's all in the rules. Or most of it is....
...you just have a lot more slack to fuck up in.
In your warehouse senario, every crate is tagged eight ways to sunday, if only for inventory management, but the inside is probably as light sec as you get. There simply isn't any 'infrastructure' to actually support that level of security.
This sort of stuff, security wise anyway, is really more limited to AAA R&D labs, HQ's and delta level labs. You'll find similar setups in government offices, if for less reason now.
Of course even AA corps probably use similar setups, sec wise, they just have less budget for HRT teams and the like. At that point you are dealing with third party security that gets called in, easier to cut the signal to the security provider, isolating the target. Human On-site security, at that point, would lock themselves in their offices until the threat went away. Of course, you can always get some young hotshot out to get himself killed.
The issue I have with the Wireless world, if I really wanted to take umbrage at anything, was just how easy Spoofing your datatrail supposedly is. At best all you can do is eliminate the surface trail, make them dig to actually track you down. Spoofing would practically leave a trail of it's own, the actual focus should be on why corps don't root out shadowrunners (because it takes long enough that it becomes an exercise in vengance, nothing more. And vengance isn't cost effective...).
The way I'd use this, btw, is simple. Let the players encounter, on an otherwise ordinary Run against an only sorta-hard target, run into a sec team with two E-War guys in it. The first time their PAN's get turned against them they'll figure out their own way to avoid it in the future, and it's all in the rules. Or most of it is....
Folks talk about security "after hours".
I'm guilty of it myself.
In the world of the 2060s-70s, is there an "after hours"?
Why not have a facility in use 24-7? What is the business sense of leaving a resource vacant in a high-tech global economy? At midnight in New York, it's daylight in Japan. And your bosses in Tokyo would like to be able to call your office and have someone answer.
I see multiple shifts spreading to more than just factory, customer service, and retail jobs.
I'm guilty of it myself.
In the world of the 2060s-70s, is there an "after hours"?
Why not have a facility in use 24-7? What is the business sense of leaving a resource vacant in a high-tech global economy? At midnight in New York, it's daylight in Japan. And your bosses in Tokyo would like to be able to call your office and have someone answer.
I see multiple shifts spreading to more than just factory, customer service, and retail jobs.
The problem is do you call your bosses in Japan while they sleep?
| QUOTE (toturi) |
| The problem is do you call your bosses in Japan while they sleep? |
if the problem is big enough, yes you do.
hell, the US president can be woken up in the middle of the night if the problem is big enough.
I see it being a mix of both. Most business resources will not run 'all night'. It's not cost effective to keep more than a skeleton crew on board. Seattle to Japan is only, what?, 6 hours difference?
That said, I'm sure that a major corporate headquarters will have people working 18 hours a day in it, with the peak being the 7-5 area. This is more true in Japanese corporations, where the office, and co-workers, are thought of as a 'second home/family' traditionally, and where it is expected for the wage earner to sacrifice his home life to provide a good life for his children. I would expect that the Seattle offices of a Japancorp have a great number of Japanese 'Salarymen' whose families actually live in Japan, and these guys literally have no where to go at night. If they rate an actual office, sleeping on the couch is a two or three night a week affair and 'home' consists of a one room apartment in a corporate hab-block, a place to change clothes almost.
Hell, even Vegas becomes a Ghost town after 2 AM, by four all you see are the gambling addicts and the craps table workers, and they are pretty much confined to the actual gambling halls, not walking the offices of the casinos.
Now, a black R&D facility? Might be another story. People constantly working, monitoring the hot projects. Sure, the night shifts are smaller, leaner... all the big brains go home eventually (where that home is, probably a secure location on site), and they like to stick together for brainstorming, leaving the grunt work scientists and techs to do less important work. But still busy, certainly. A run on such a site is going to be messy regardless of what time it is.
That said, I'm sure that a major corporate headquarters will have people working 18 hours a day in it, with the peak being the 7-5 area. This is more true in Japanese corporations, where the office, and co-workers, are thought of as a 'second home/family' traditionally, and where it is expected for the wage earner to sacrifice his home life to provide a good life for his children. I would expect that the Seattle offices of a Japancorp have a great number of Japanese 'Salarymen' whose families actually live in Japan, and these guys literally have no where to go at night. If they rate an actual office, sleeping on the couch is a two or three night a week affair and 'home' consists of a one room apartment in a corporate hab-block, a place to change clothes almost.
Hell, even Vegas becomes a Ghost town after 2 AM, by four all you see are the gambling addicts and the craps table workers, and they are pretty much confined to the actual gambling halls, not walking the offices of the casinos.
Now, a black R&D facility? Might be another story. People constantly working, monitoring the hot projects. Sure, the night shifts are smaller, leaner... all the big brains go home eventually (where that home is, probably a secure location on site), and they like to stick together for brainstorming, leaving the grunt work scientists and techs to do less important work. But still busy, certainly. A run on such a site is going to be messy regardless of what time it is.
EDIT: I think my reply makes more sense as the start of a new topic. Reply is here.
Having just come back from Vegas I can tell you it is still pretty pumping after 2 am and not just in the gambling halls. I left Tao at 1:30 and walked the Strip for half an hour before going to bed and some people were JUST starting to leave for clubs/strip clubs/wherever they were going.
A 24 hour facility does make sense depending on what it is for. Retail no. Finance, hell yeah! Especially if you don't have an office in whichever country you are trading in. Of course even if you do it is still better to have more people looking at the same stuff. Diversification can reduce all risks, including analysis/modelling error. 24 hour sales? Why not. Most of the telemarketing calls I get in RL come from India (about 14 hours difference) or at least from Toronto (3 hour difference).
How about timeshare on your cubicle? During the day the whole office gets turned over to the trading pit, and when the exchange closes in come the data entry specialists to do the daily reconciliations and A/P. Maybe even you lease some of the space out for other uses. In RL we already have night clubs on the higher floors of sky scrapers. With the portability of info in SR you could easily take down an office at say 2000, open the club at 2200, keep it open until 0400 the next day, and have the office up and running by 0600 again.
A 24 hour facility does make sense depending on what it is for. Retail no. Finance, hell yeah! Especially if you don't have an office in whichever country you are trading in. Of course even if you do it is still better to have more people looking at the same stuff. Diversification can reduce all risks, including analysis/modelling error. 24 hour sales? Why not. Most of the telemarketing calls I get in RL come from India (about 14 hours difference) or at least from Toronto (3 hour difference).
How about timeshare on your cubicle? During the day the whole office gets turned over to the trading pit, and when the exchange closes in come the data entry specialists to do the daily reconciliations and A/P. Maybe even you lease some of the space out for other uses. In RL we already have night clubs on the higher floors of sky scrapers. With the portability of info in SR you could easily take down an office at say 2000, open the club at 2200, keep it open until 0400 the next day, and have the office up and running by 0600 again.
getting back to the original topic, i have come to the conclusion that there is one piece of gear that no runner can afford to go without. fortunately, it's exceptionally inexpensive.
| QUOTE (SR4 @ page 319, "stealth tags") |
| Stealth Tags: Stealth tags are encoded to remain silent and only respond to transmissions with the proper passcodes. They cannot be located with a commlink or bug scanner (unless the codes are known). |
there you go, problem solved. no more luddite ninjas required, no more e-war commandos required, just one person willing to blow 5
you may now go back to your regular DSF sidetracked discussion about 24 hour facilities
nice call. doesn't give you quite as much functionality as networked comms but solves the problem. Thanks Jaid.
RFID Tags generally have only a Signal Rating of 1.
| QUOTE (Rotbart van Dainig) |
| RFID Tags generally have only a Signal Rating of 1. |
stealth tags generally have a signal rating of 6. it's right in the table, don't look at me
and why wouldn't this give the benefit of networked comms cheops? you're just routing all your wireless traffic through the undetectable stealth tag. your PAN is still doing all the work, the stealth tags are just signal repeaters that transmit between the team. they get info from your PAN through a wire, and broadcast it to your teammate's stealth tags. the stealth tags that your teammates have will then transmit to your teammate's PAN by wired connection of some sort. your teammates then send info back through the same route, only reversed.
| QUOTE (Jaid) | ||
stealth tags generally have a signal rating of 6. it's right in the table, don't look at me |
They have a Device Rating of 3, and a Signal of 1. (Device Ratings are superseeded by specific Matrix Attributes.)
The column you are refering to is labeled 'Availability' for 'Acessory' and below.
| QUOTE (Rotbart van Dainig) | ||||
They have a Device Rating of 3, and a Signal of 1. (Device Ratings are superseeded by specific Matrix Attributes.) The column you are refering to is labeled 'Availability' for 'Acessory' and below. |
wrong page 319 4th printing says stealth id tags have a signal of 6 and a response of 3.
check your errata mate.
| QUOTE (Rotbart van Dainig) | ||||
They have a Device Rating of 3, and a Signal of 1. (Device Ratings are superseeded by specific Matrix Attributes.) The column you are refering to is labeled 'Availability' for 'Acessory' and below. |
hmmm... actually, you got me there, didn't check further down and see the column change to availability from signal... either way, stealth tags are not necessarily limited to signal 1 because of the limitations of regular RFIDs...
| QUOTE (silentmaster101 @ May 11 2007, 09:33 PM) | ||||||
wrong page 319 4th printing says stealth id tags have a signal of 6 and a response of 3. check your errata mate. |
You may take a look at the Errata - it doesn't say so.
Until the PDF v4 gets out, I'll stick with PDF v3 + Errata 1.5.
that being said, an upgrade to signal 4 (1km range, and with ECCM 3 requires rating 8 wireless inhibiting material) would cost a mere 500 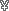 per runner. if you need more range than that, than i would hazard a guess you don't need to conceal your communications that badly anyways
per runner. if you need more range than that, than i would hazard a guess you don't need to conceal your communications that badly anyways 
(though if you still do, rating 6 is only 3,000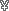 which isn't that bad, and brings the jamming/wifi inhibiting requirement back up to 10)
which isn't that bad, and brings the jamming/wifi inhibiting requirement back up to 10)
(though if you still do, rating 6 is only 3,000
| QUOTE (Rotbart van Dainig) | ||||||||
You may take a look at the Errata - it doesn't say so. Until the PDF v4 gets out, I'll stick with PDF v3 + Errata 1.5. |
uh i have the pdf version of 4th printing.....
| QUOTE (silentmaster101) |
| uh i have the pdf version of 4th printing..... |
That's interesting.
Where from?
And, more important - does Adam know about that?
i think i got it off amazon, IIRC. wasnt too long ago, maybe a month or so.
edit: might be v3, im looking at the hardback book right now so im a bit fuzzy on it.
edit: might be v3, im looking at the hardback book right now so im a bit fuzzy on it.
i wonder what the difference between the stealth tag and a comlink on hidden is...
This is a "lo-fi" version of our main content. To view the full version with more information, formatting and images, please click here.